2023 楚慧杯网络空间安全实践能力竞赛 Misc Writeup
2023 楚慧杯网络空间安全实践能力竞赛 Misc Writeup
本文中涉及的具体题目附件可以进我的交流群获取,进群详见 About
题目名称 ez_zip
解压附件得到一个4096.zip,打开发现有一个4095.zip,因此猜测是压缩包套娃
直接写个Python脚本解套即可
| |
全部解压完后可以得到一个1.txt,内容如下
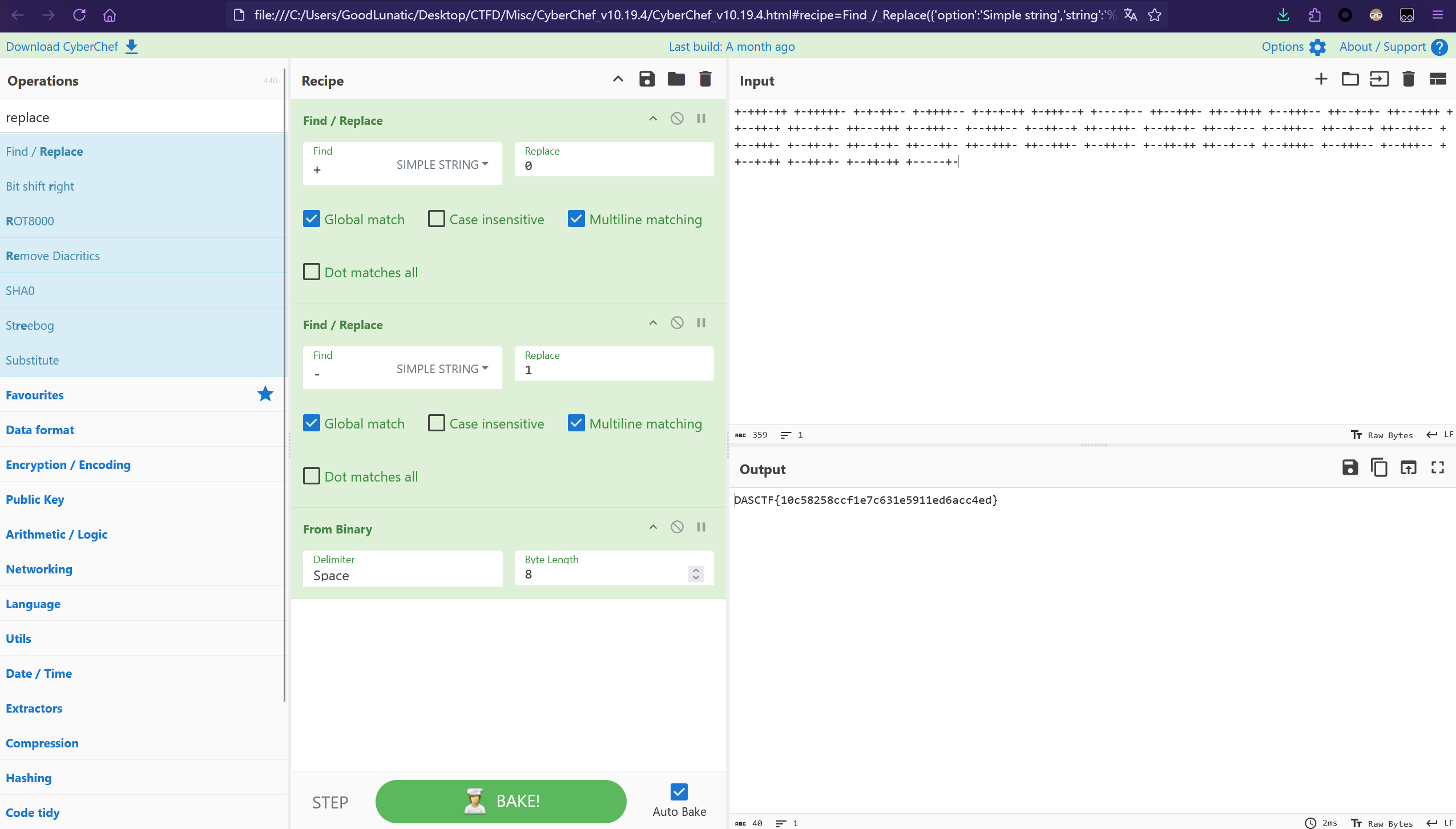
+-+++-++ +-+++++- +-+-++– +-++++– +-+-+-++ +-+++–+ +—-+– ++–+++- ++–++++ +–+++– ++–+-+- ++—+++ ++–++-+ ++–+-+- ++—+++ +–+++– +–+++– +–++–+ ++–+++- +–++-+- ++–+— +–+++– ++–+–+ ++–++– ++–+++- +–++-+- ++–+-+- ++—++- ++–+++- ++–+++- +–++-+- +–++-++ ++–+–+ +–++++- +–+++– +–+++– ++–+-++ +–++-+- +–++-++ +—–+-
直接CyberChef转二进制,然后转字符串即可得到flag:DASCTF{10c58258ccf1e7c631e5911ed6acc4ed}
题目名称 easy取证
下载附件并解压,得到一个mem.raw内存镜像,直接使用vol2进行内存取证
在桌面上可以找到一个机密.docx,尝试导出
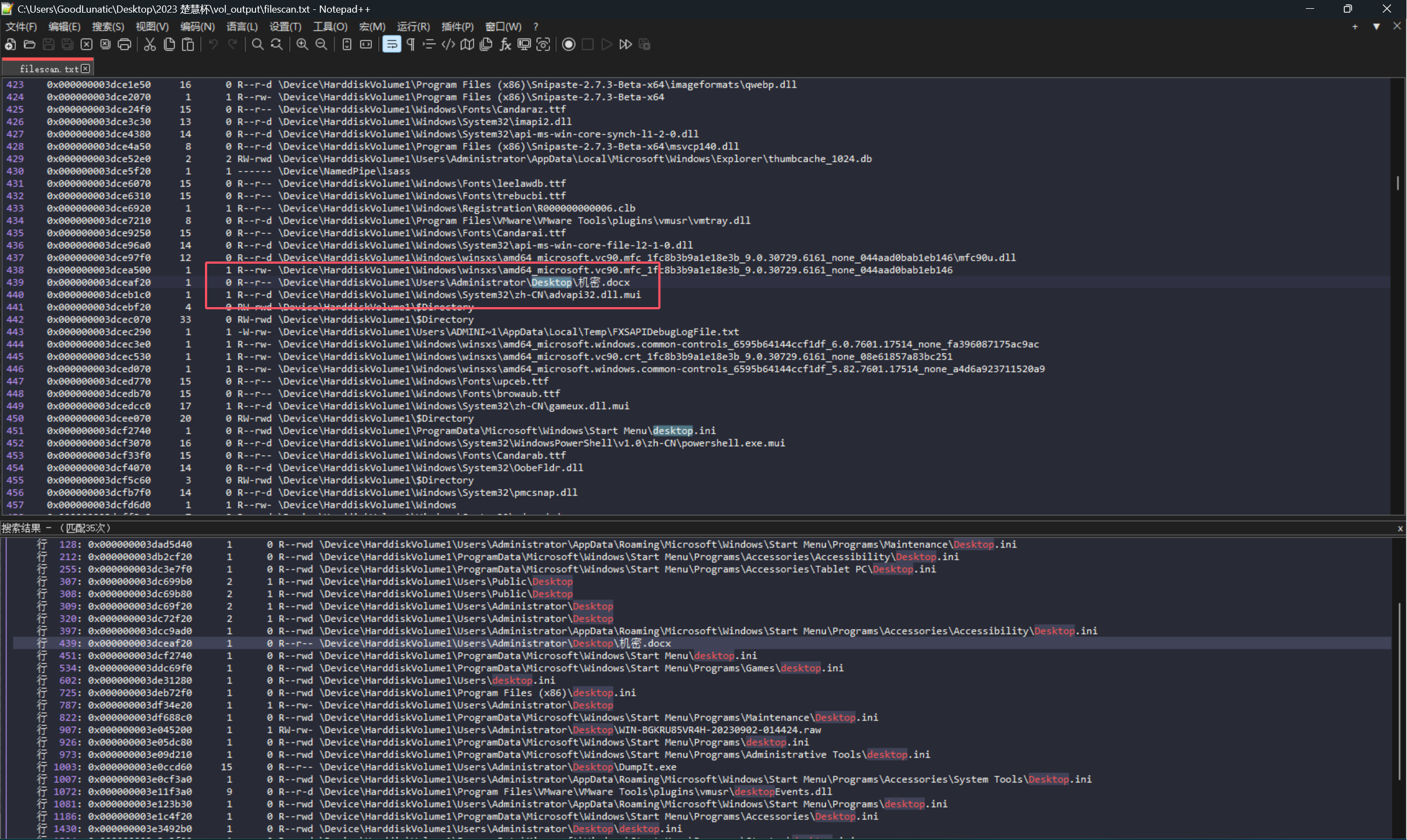
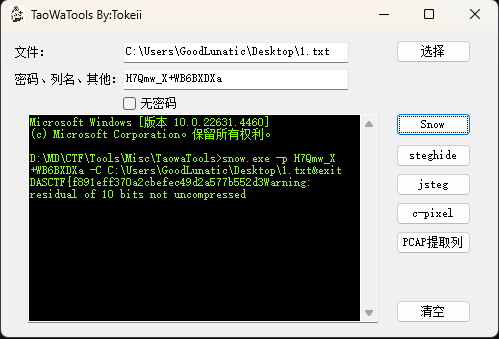
导出后打开,发现是一个只有空白字符的文档,猜测是SNOW隐写
把所有空白字符复制到TXT文件中,尝试直接使用无密码的SNOW解密,但是发现得不到有效信息
用mimikatz插件可以提取出用户名和密码
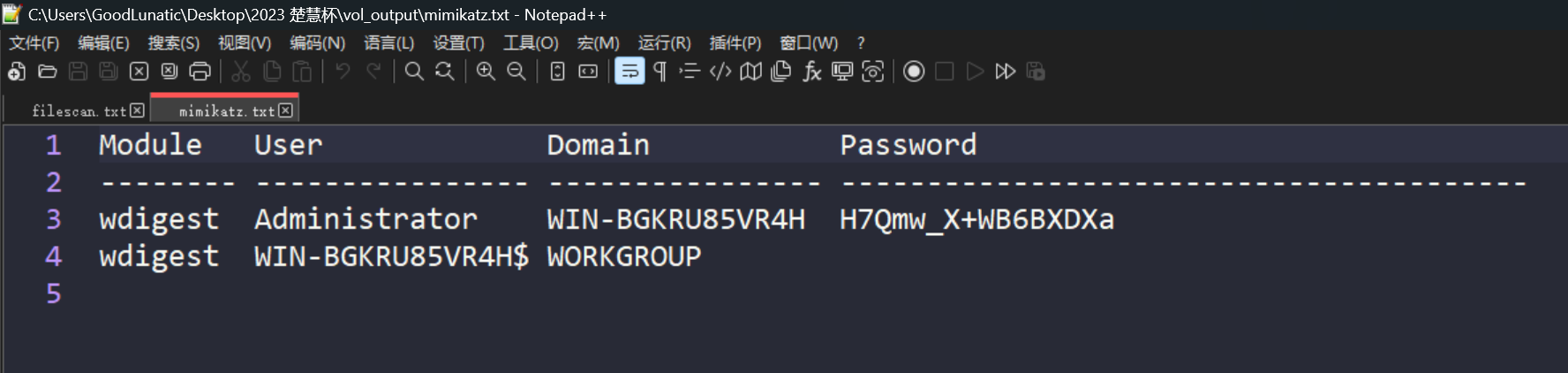
使用得到的密码H7Qmw_X+WB6BXDXa解密SNOW隐写即可得到flag:DASCTF{f891eff370a2cbefec49d2a577b552d3}
题目名称 gb2312-80
下载附件并解压,可以得到如下内容
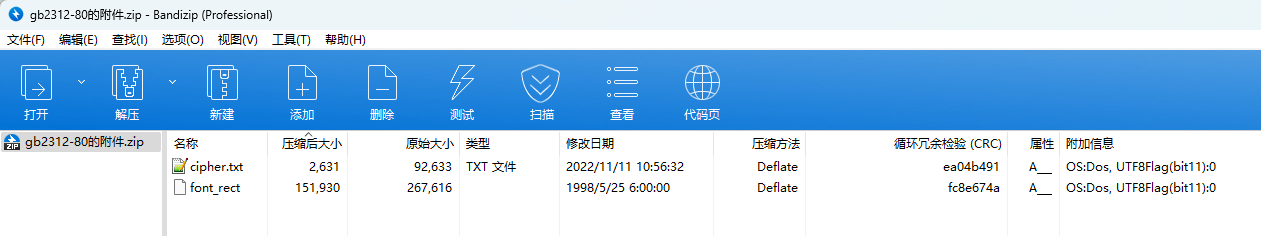
cipher.txt中的内容如下,每行十六个元素
| |
然后去网上搜索font_rect,可以找到这个项目,发现是画点阵图的项目,并且图片大小是16x16的
正好与附件所给的数据格式相符,因此我们尝试写一个脚本画一下点阵图
| |
画完后发现一共就16种图像,因此猜测是十六进制的数据
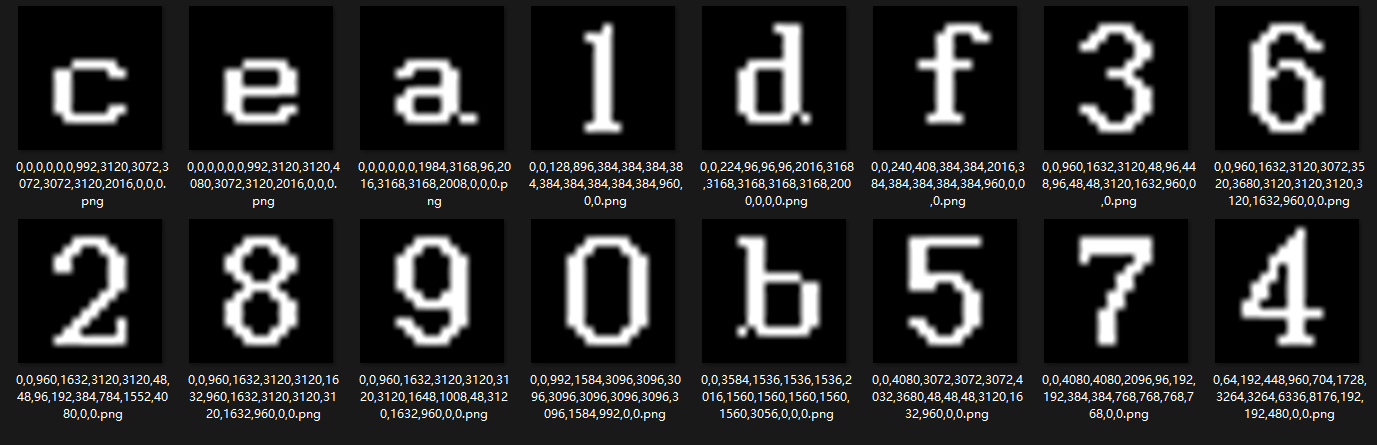
我们根据上面的图片找出对应的表,然后提取出十六进制的数据,查看头几个数据就可以发现是个压缩包
因此我们编写以下脚本把压缩包提取出来
| |
压缩包中有以下两个文件
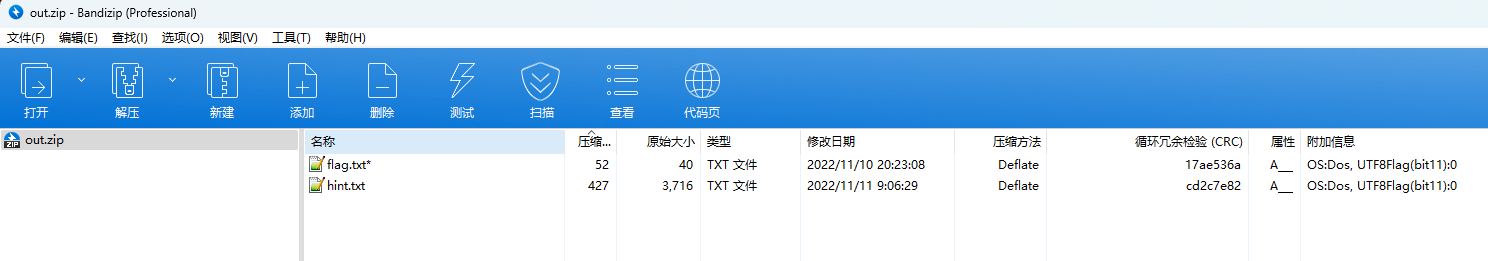
flag.txt需要密码才能解压,hint.txt的内容如下
| |
猜测和上面一样,需要画点阵图,因此我们编写以下脚本画一下点阵图
| |
画完后即可得到解压密码:ILOVEHZK16

使用得到的密码解压压缩包即可得到flag:DASCTF{842a99305a07e6183830582d1740c1b1}
完整解题脚本如下:
| |
 Lunatic
Lunatic