2024 国城杯网络安全挑战赛 Misc Writeup
忙里抽闲,简单地看了看题,感觉这场比赛的取证确实出得挺好的
给取证题 Just_F0r3n51Cs 的出题人点个赞👍
 |
|---|
| 题目附件下载: https://pan.baidu.com/s/10jfYCo2y19sFcZyQoAgv2g?pwd=gu59 提取码: gu59 |
线上初赛
题目名称 Tr4ffIc_w1th_Ste90
解压附件压缩包,可以得到一个流量包和一个加密的压缩包
打开流量包,发现主要是UDP流量,然后还有H264的视频数据
直接追踪UDP流,复制原始Hex数据,用Cyberchef转换一下
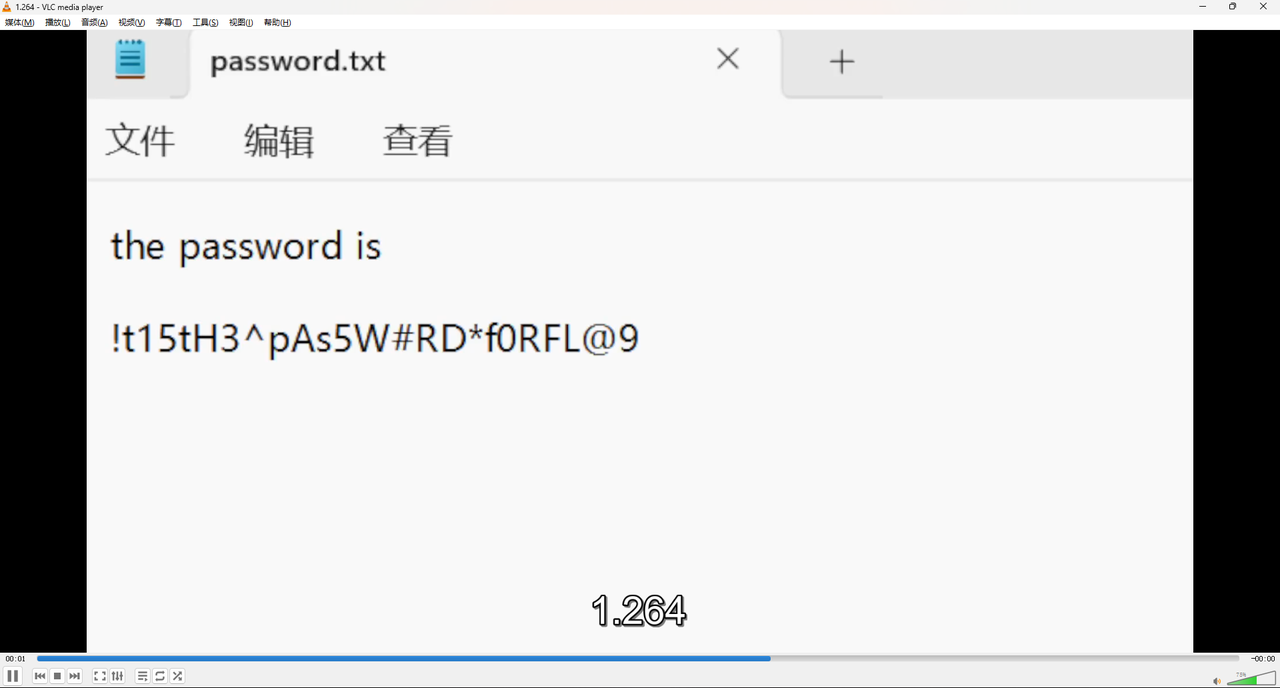
然后下载到本地改后缀为.264,VLC打开即可得到压缩包的解压密码:!t15tH3^pAs5W#RD*f0RFL@9
解压压缩包可以得到一张图片和加密图片的代码,遛一遛GPT写一个解密代码
|
|
运行上面的脚本爆破一下seed
|
|
然后可以得到一张DataMatrix二维码

在线网站扫码可以得到如下内容
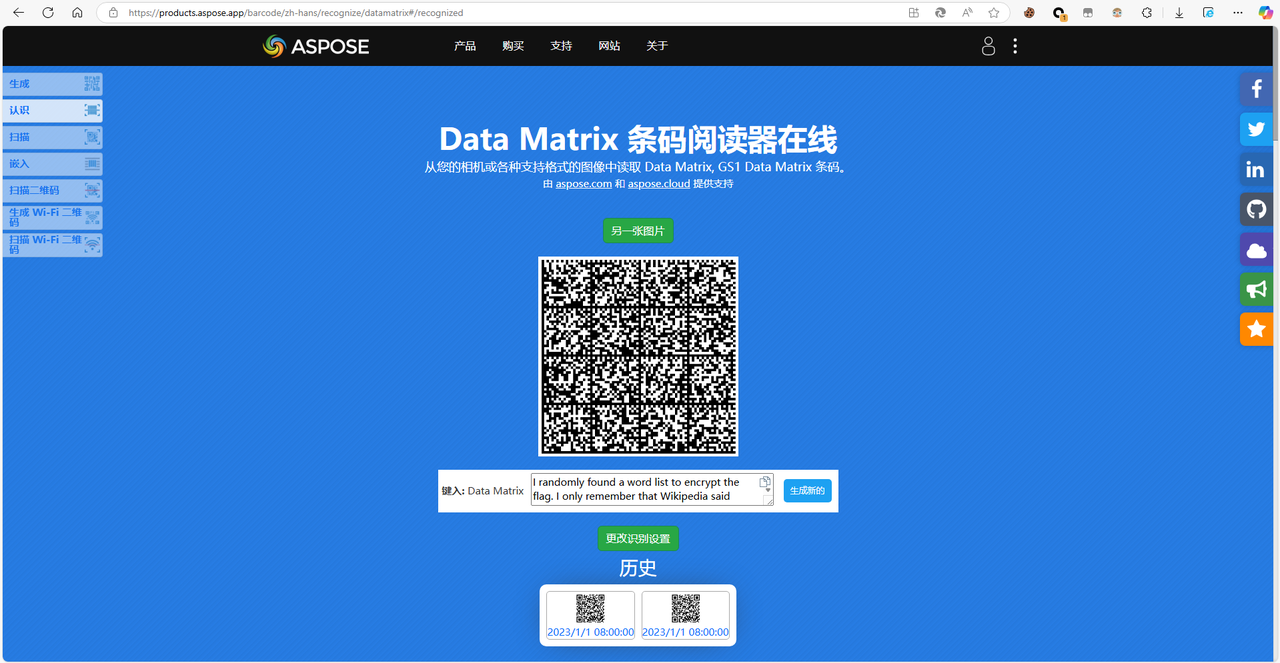
I randomly found a word list to encrypt the flag. I only remember that Wikipedia said this word list is similar to the NATO phonetic alphabet.
crumpled chairlift freedom chisel island dashboard crucial kickoff crucial chairlift drifter classroom highchair cranky clamshell edict drainage fallout clamshell chatter chairlift goldfish chopper eyetooth endow chairlift edict eyetooth deadbolt fallout egghead chisel eyetooth cranky crucial deadbolt chatter chisel egghead chisel crumpled eyetooth clamshell deadbolt chatter chopper eyetooth classroom chairlift fallout drainage klaxon
最后找个PGP词汇表解密脚本解密即可得到flag:D0g3xGC{C0N9rA7ULa710n5_Y0U_HaV3_ACH13V3D_7H15_90aL}
|
|
参考链接:https://gryffinbit.top/2020/11/14/%E4%B8%80%E4%BA%9B%E6%9D%82%E4%B9%B1%E7%9A%84%E5%AF%86%E7%A0%81/#PGP%E8%AF%8D%E6%B1%87%E8%A1%A8-%EF%BC%88%E7%94%9F%E7%89%A9%E8%AF%86%E5%88%AB%E8%AF%8D%E6%B1%87%E8%A1%A8%EF%BC%89
题目名称 Just_F0r3n51Cs
题目附件给了一个E01的磁盘镜像,可以使用FTK image进行挂载
虽然会提示报错,但是依旧是可以成功挂载的
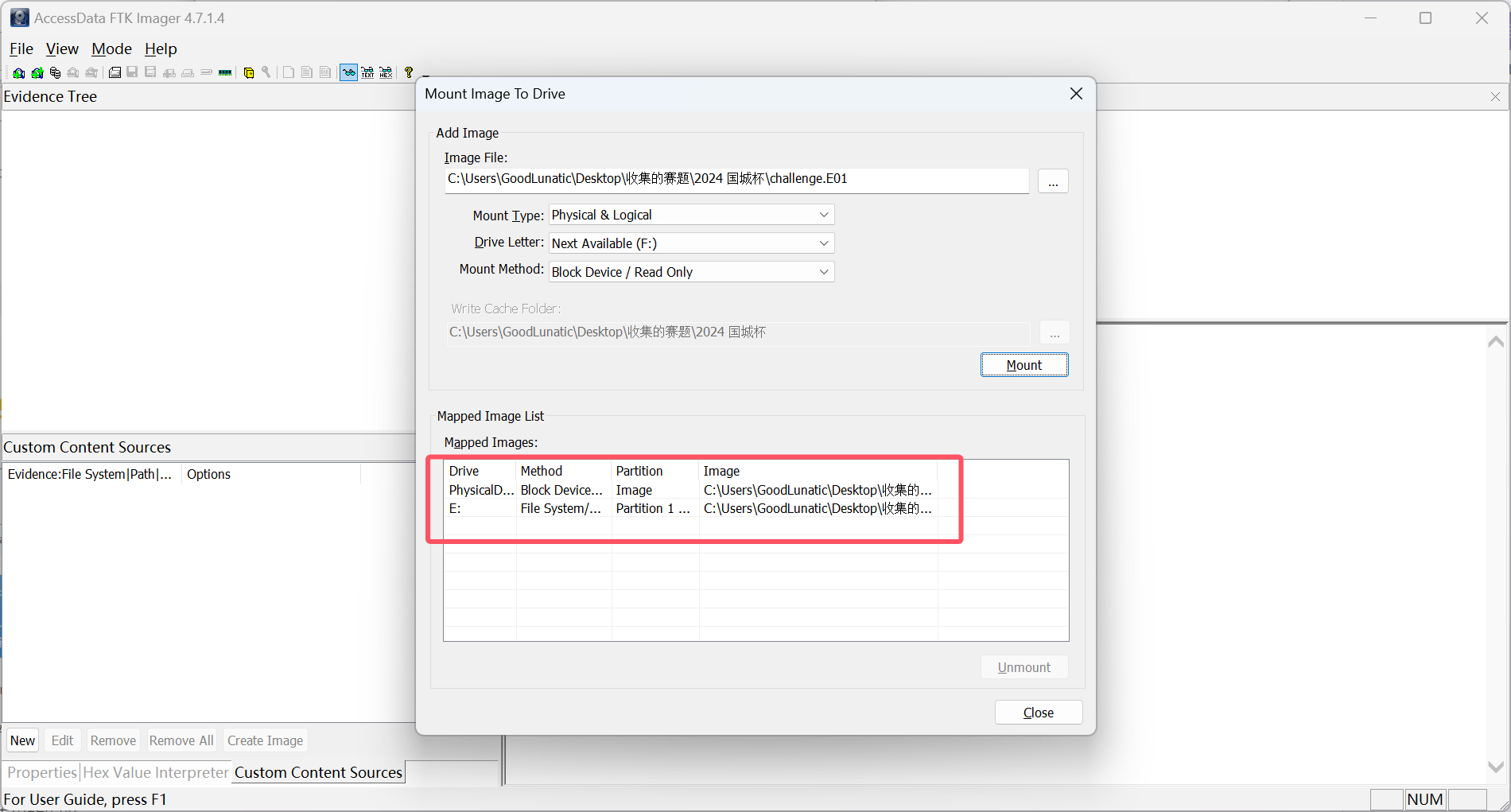
挂载成功后,看用户目录下的桌面文件夹,有一个流量包文件
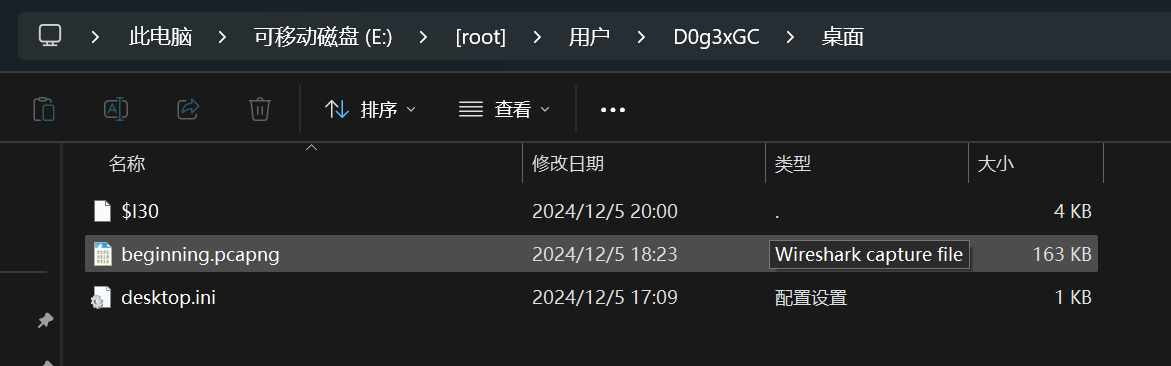
翻看流量包,发现主要是HTTP和OICQ流量,HTTP流量中可以导出下面这张JPG图片

010打开,发现末尾给了提示
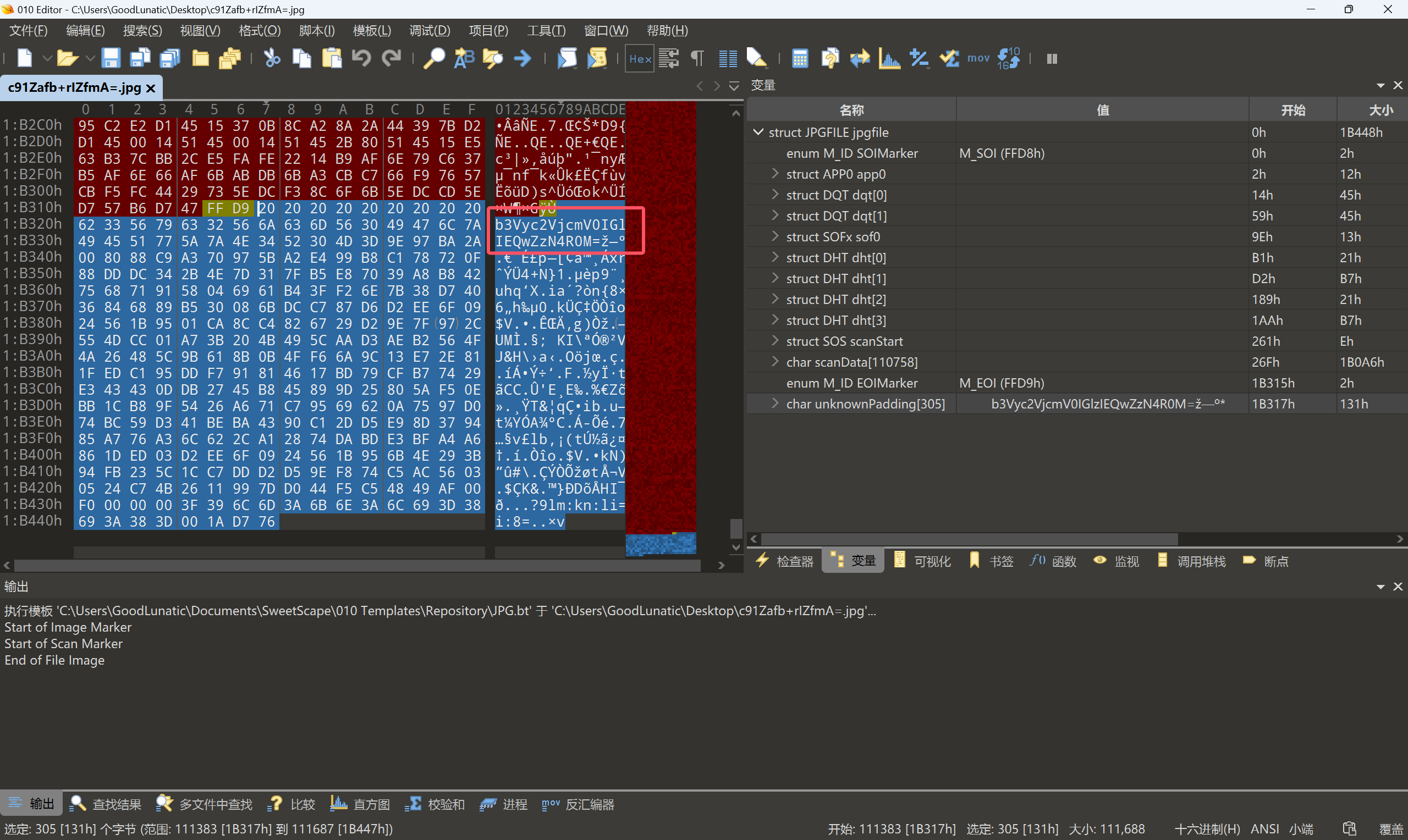
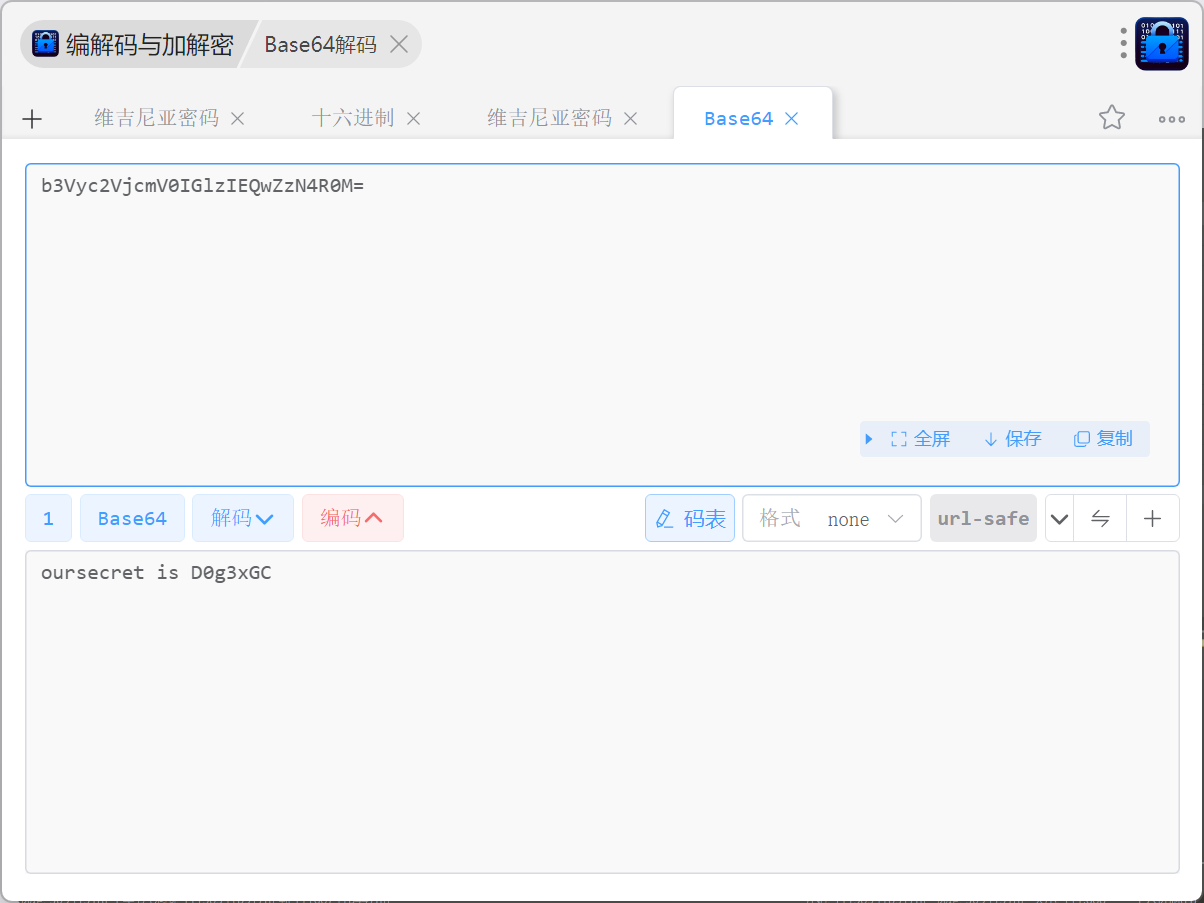
base64解码可以得到:oursecret is D0g3xGC
因此猜测这张JPG图片用oursecret隐写了信息,尝试用D0g3xGC作为密钥进行提取
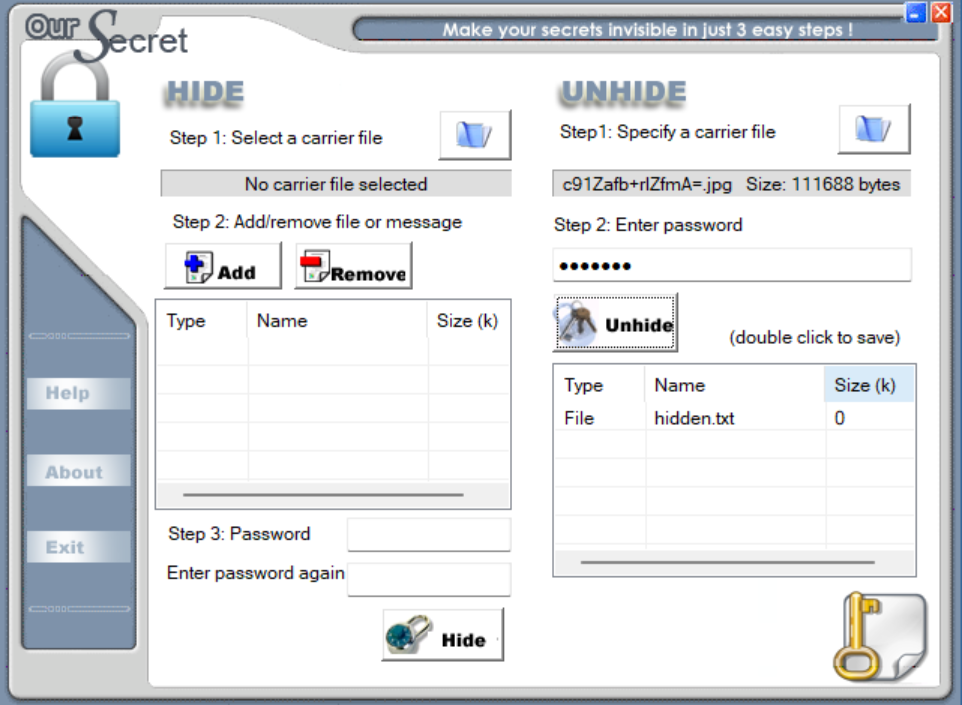
可以得到一个hidden.txt,内容如下
ECB’s key is
N11c3TrYY6666111
记得给我秋秋空间点赞
给了密钥,并提示密文在QQ空间里,因此我们需要分析流量包中OICQ协议的内容
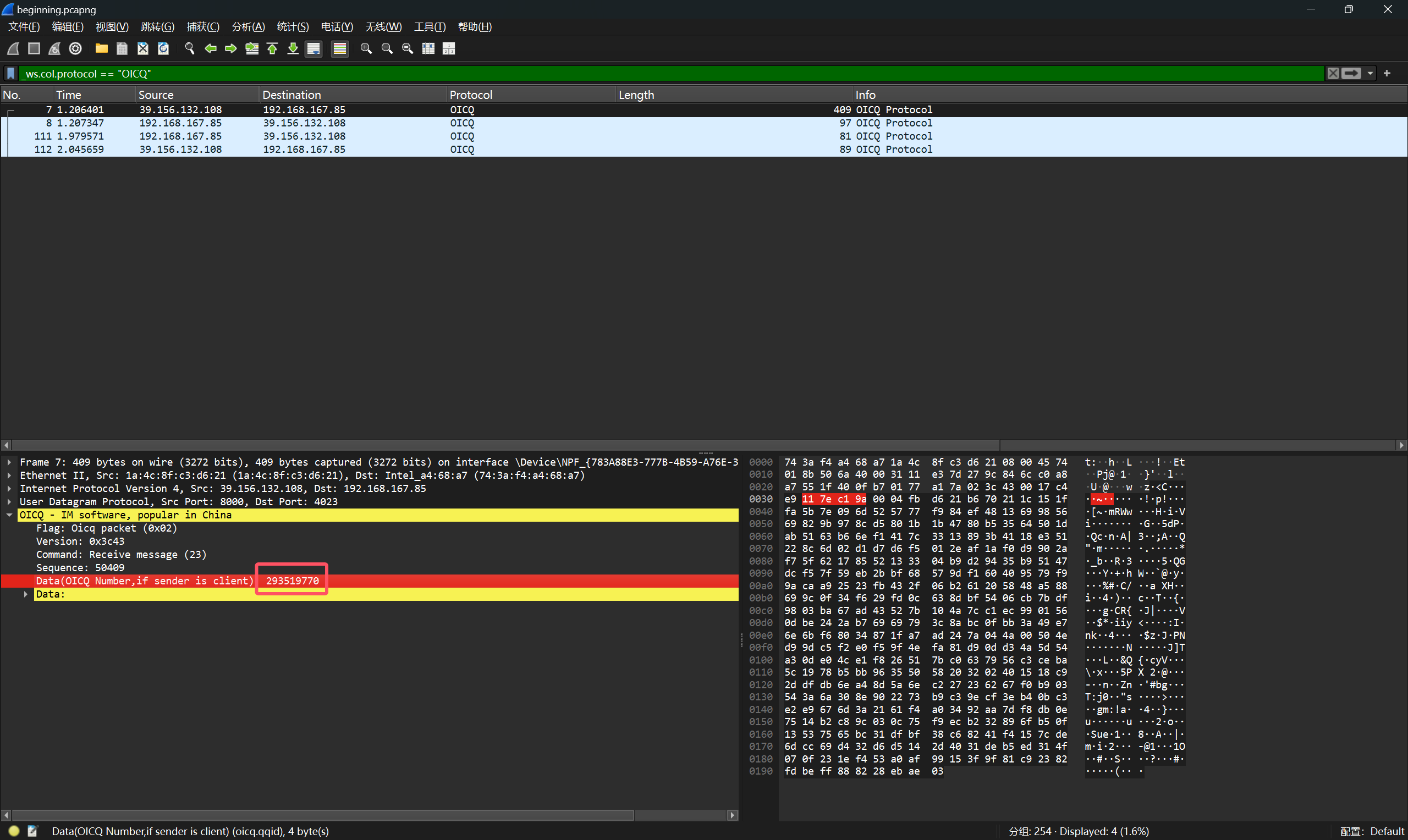
展开OICQ数据包的内容,可以得到QQ号:293519770
因此我们可以尝试访问这个人的QQ空间
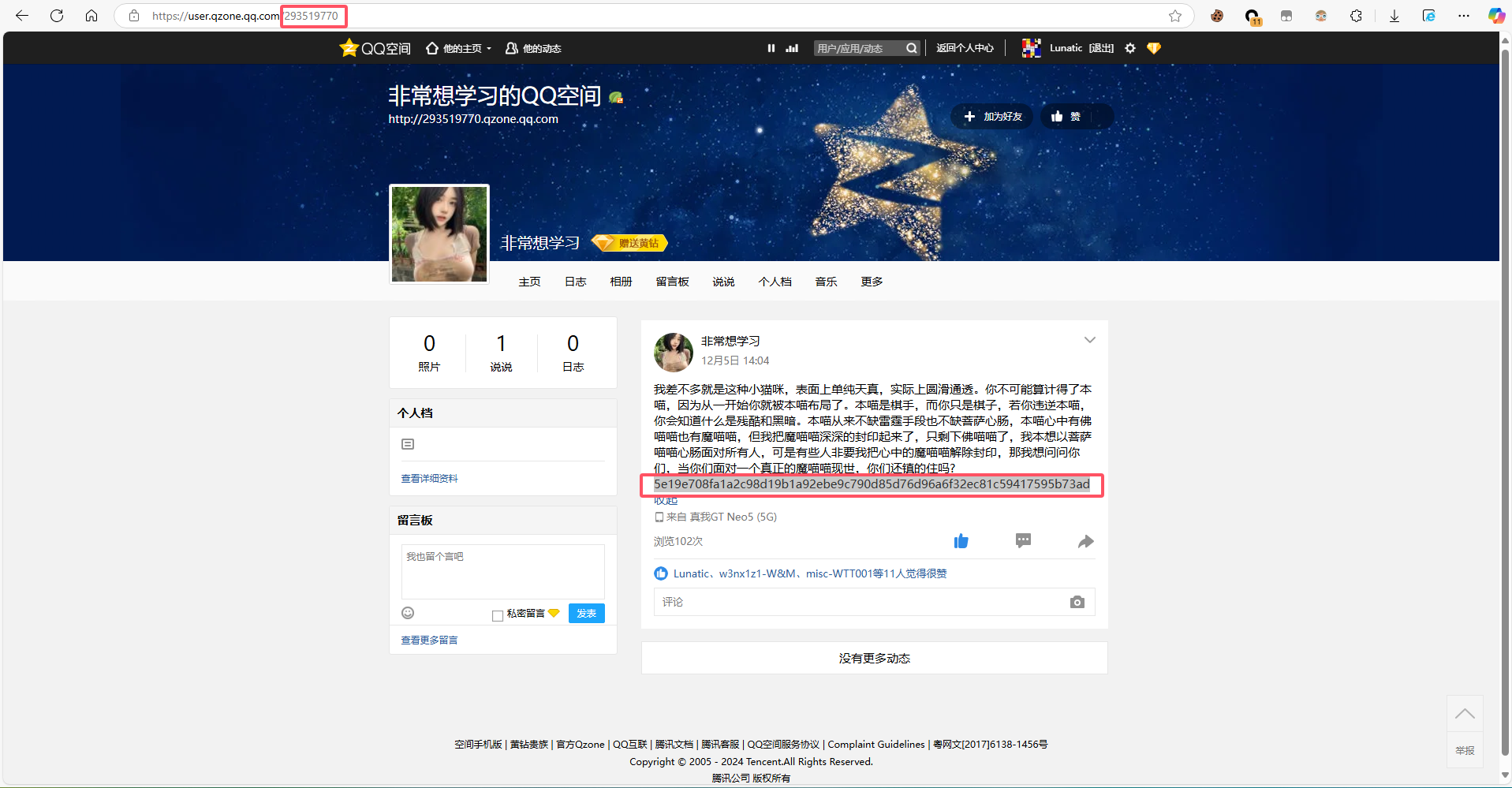
可以得到密文:
5e19e708fa1a2c98d19b1a92ebe9c790d85d76d96a6f32ec81c59417595b73ad
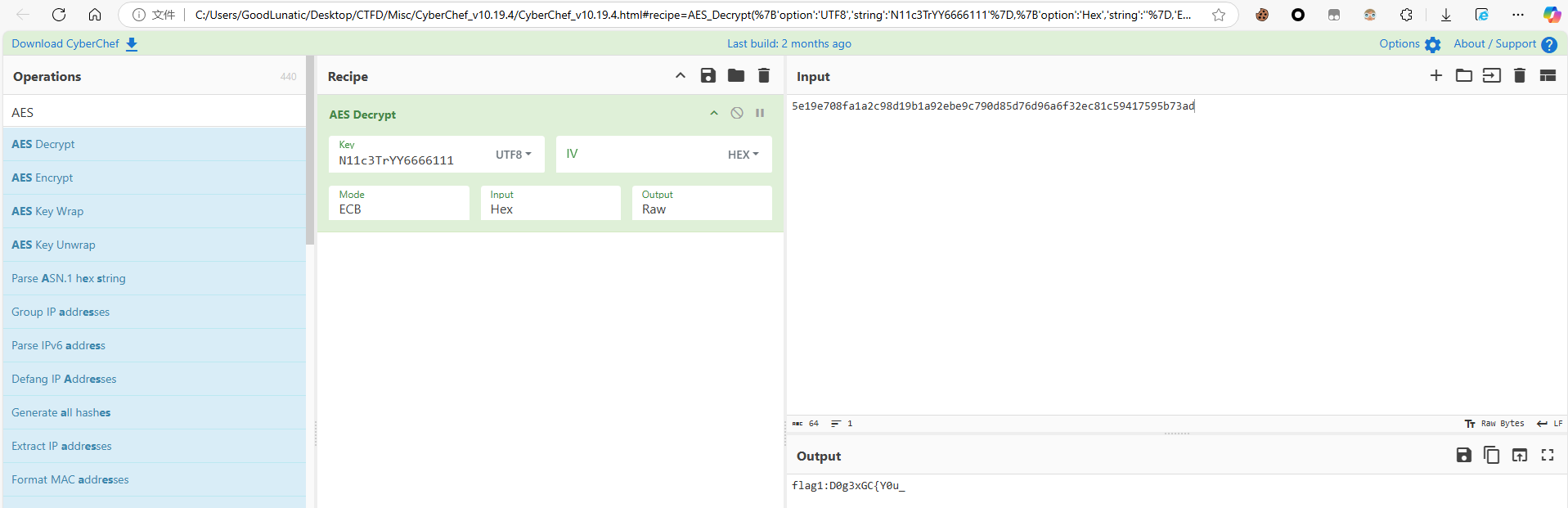
结合密文密钥,AES-ECB解密可以得到第一段的flag:flag1:D0g3xGC{Y0u_
然后我们回到刚刚挂载磁盘的用户目录下,可以发现有一个flag4.zip
提取出来并解压,可以得到如下两个文件,其中的exe是由python打包的exe文件
因此猜测需要我们逆向exe中的加密逻辑,解密出bin文件中的内容
首先我们可以使用 pyinstxtractor-ng 对exe文件进行解包得到.pyc文件
在一堆pyc文件中找到关键的enc_png.pyc,然后使用uncompyle6对pyc文件进行反编译
uncompyle6可以直接使用 pip install 进行安装
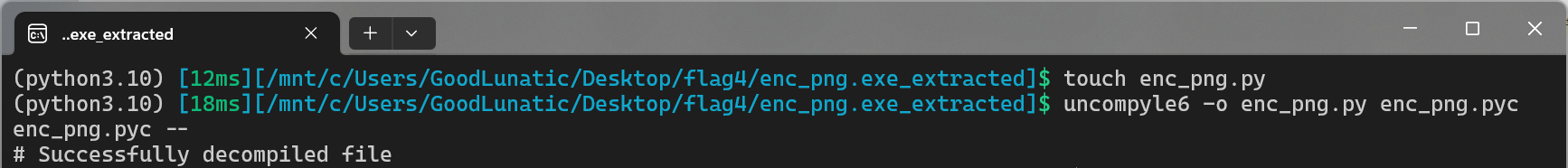
反编译成功后可以得到如下代码
|
|
其实就是一个简单的逐字节异或,看懂加密逻辑后直接CyberChef解密即可得到:F0R3N51c5_Ch4Ll3N93}
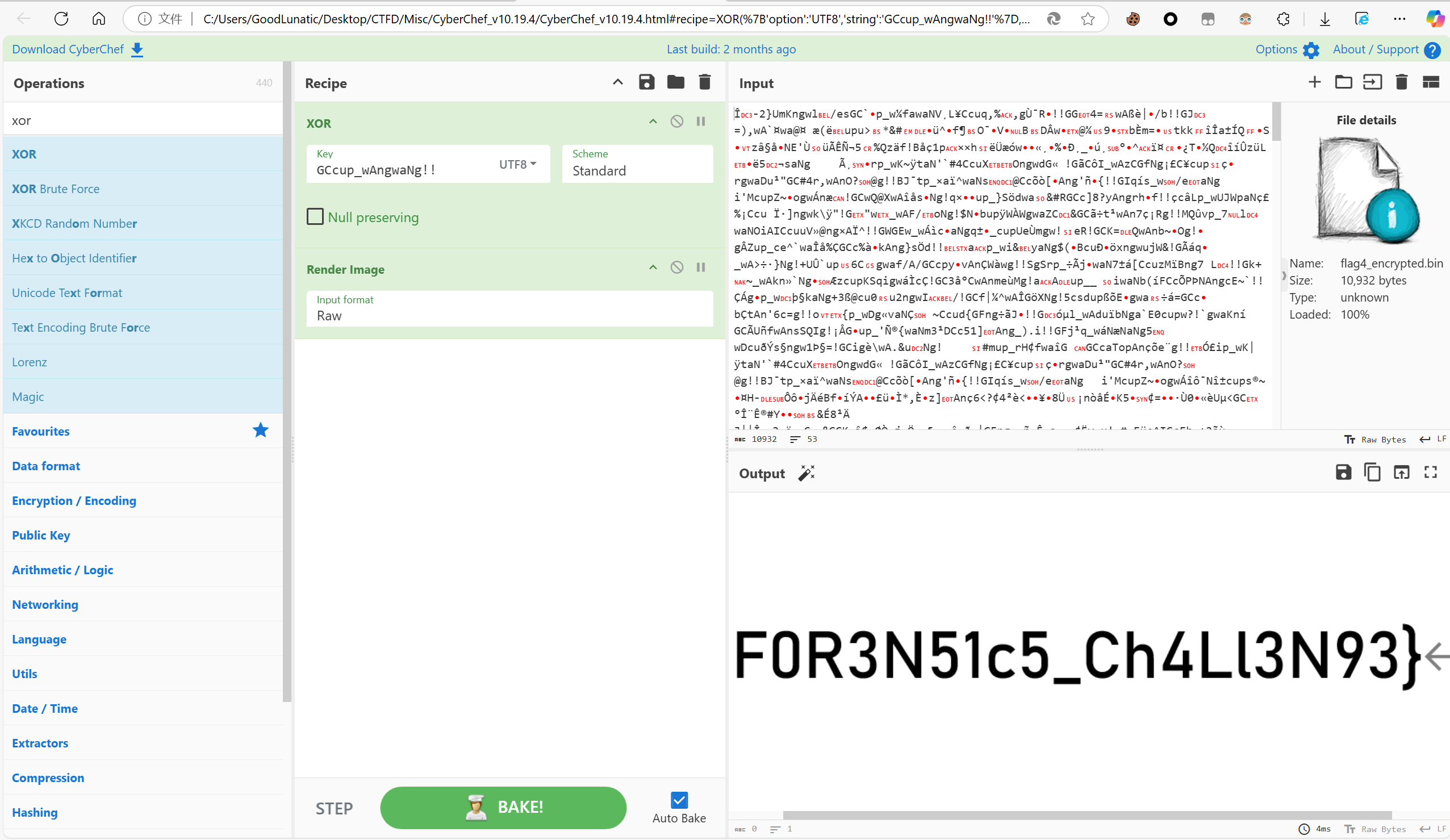
flag1和flag4可以通过FTK Image挂载并结合上述步骤获得,但是flag2和flag3就需要使用Autopsy工具进行辅助取证了
首先是查看环境变量,Windows的环境变量保存在注册表SYSTEM\CurrentControlSet001\Control\Session Manager\Environment中,注册表在C:\Windows\System32\config目录下
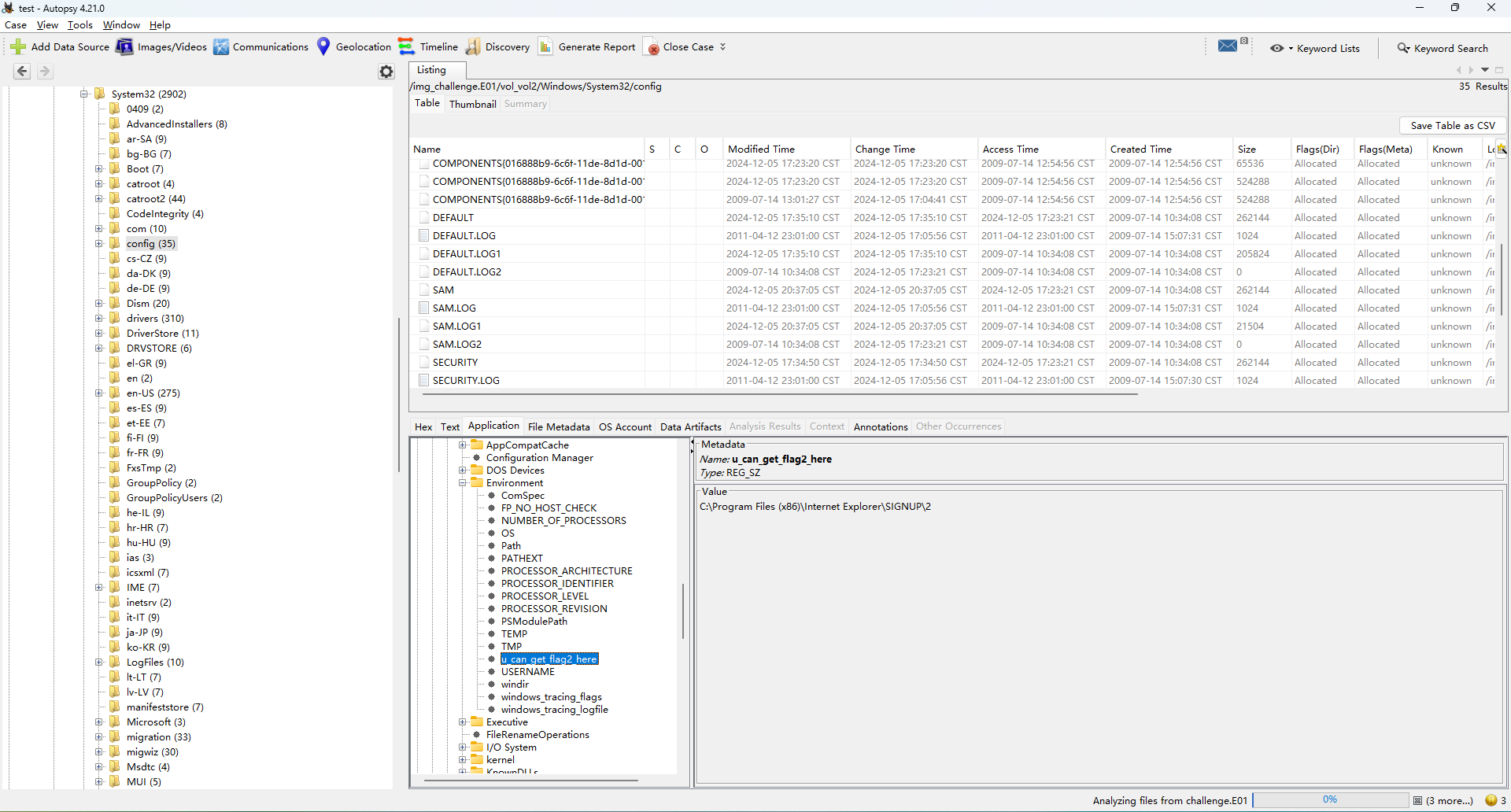
然后我们在环境变量中发现了u_can_get_flag2_here,并且它的值指向了一个文件C:\Program Files (x86)\Internet Explorer\SIGNUP\2
我们尝试把这个文件提取出来,看文件头发现是个zip压缩包
改后缀为zip并打开,发现是加密的,但是注释中有关于密码的提示
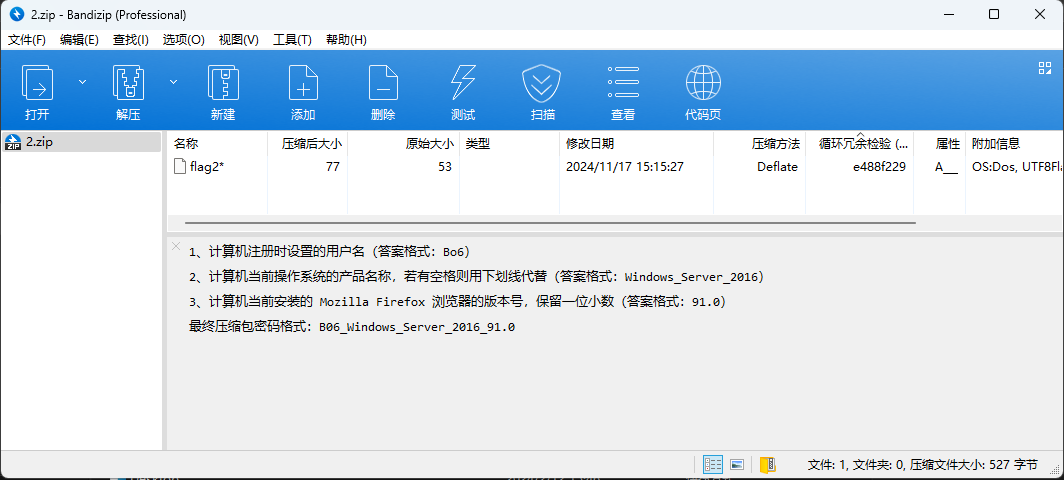
然后我们可以在注册表中寻找上述问题的答案
问题一的答案在C:\Windows\System32\Config\SOFTWARE\Microsoft\Windows NT\CurrentVersion\RegisteredOwner
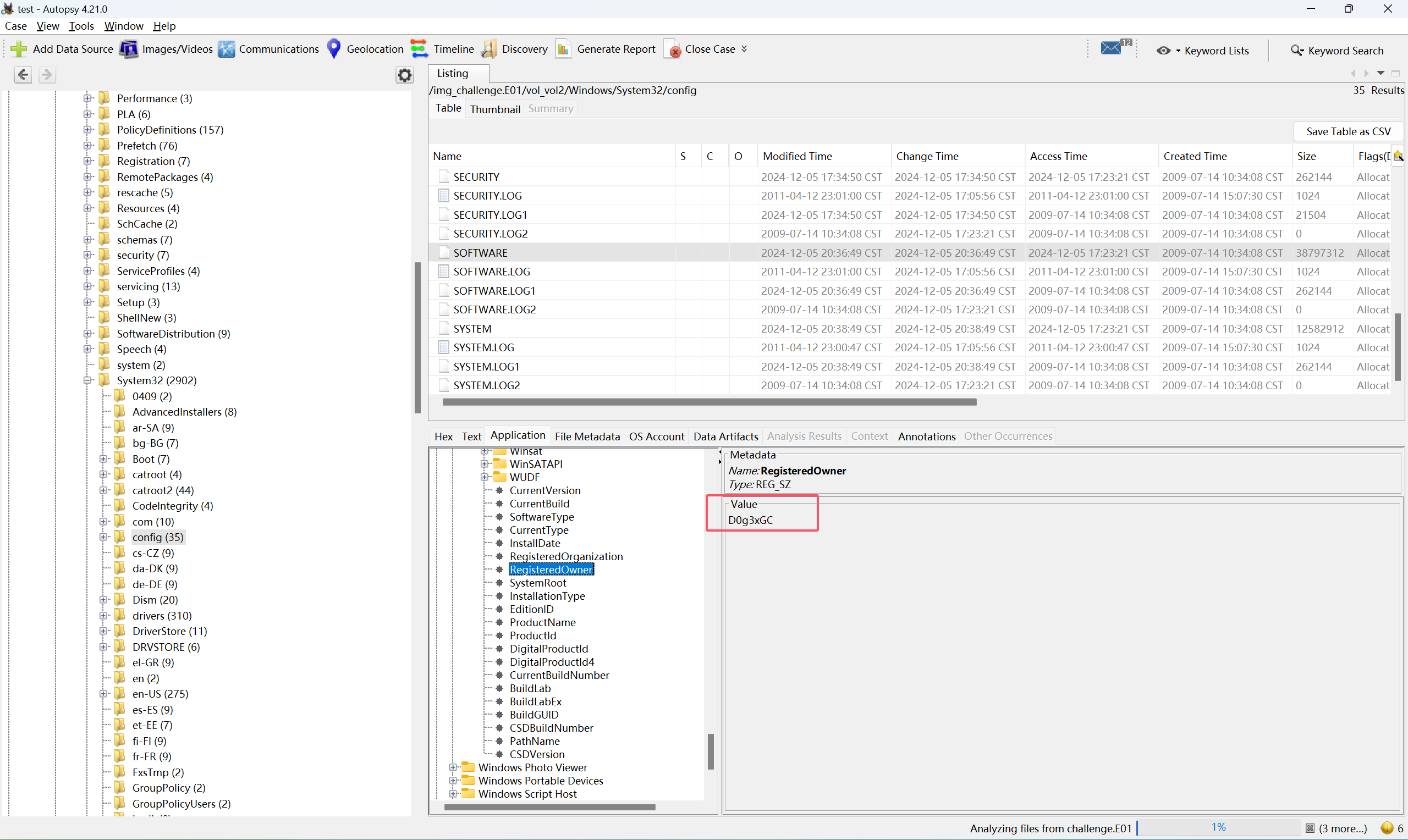
问题二的答案在C:\Windows\System32\Config\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductName
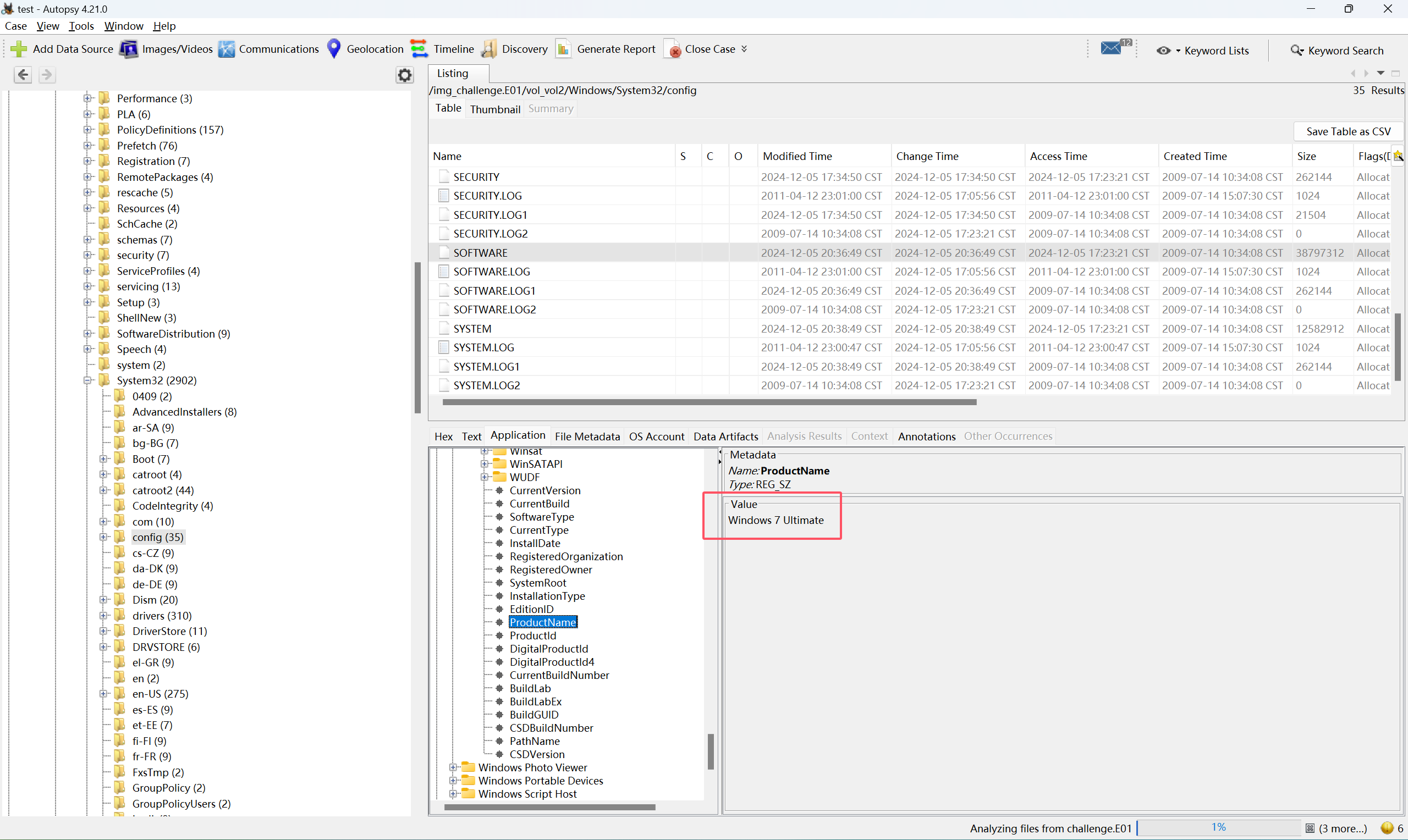
问题三的答案在C:\Windows\System32\Config\SOFTWARE\Mozilla\Mozilla Firefox\CurrentVersion
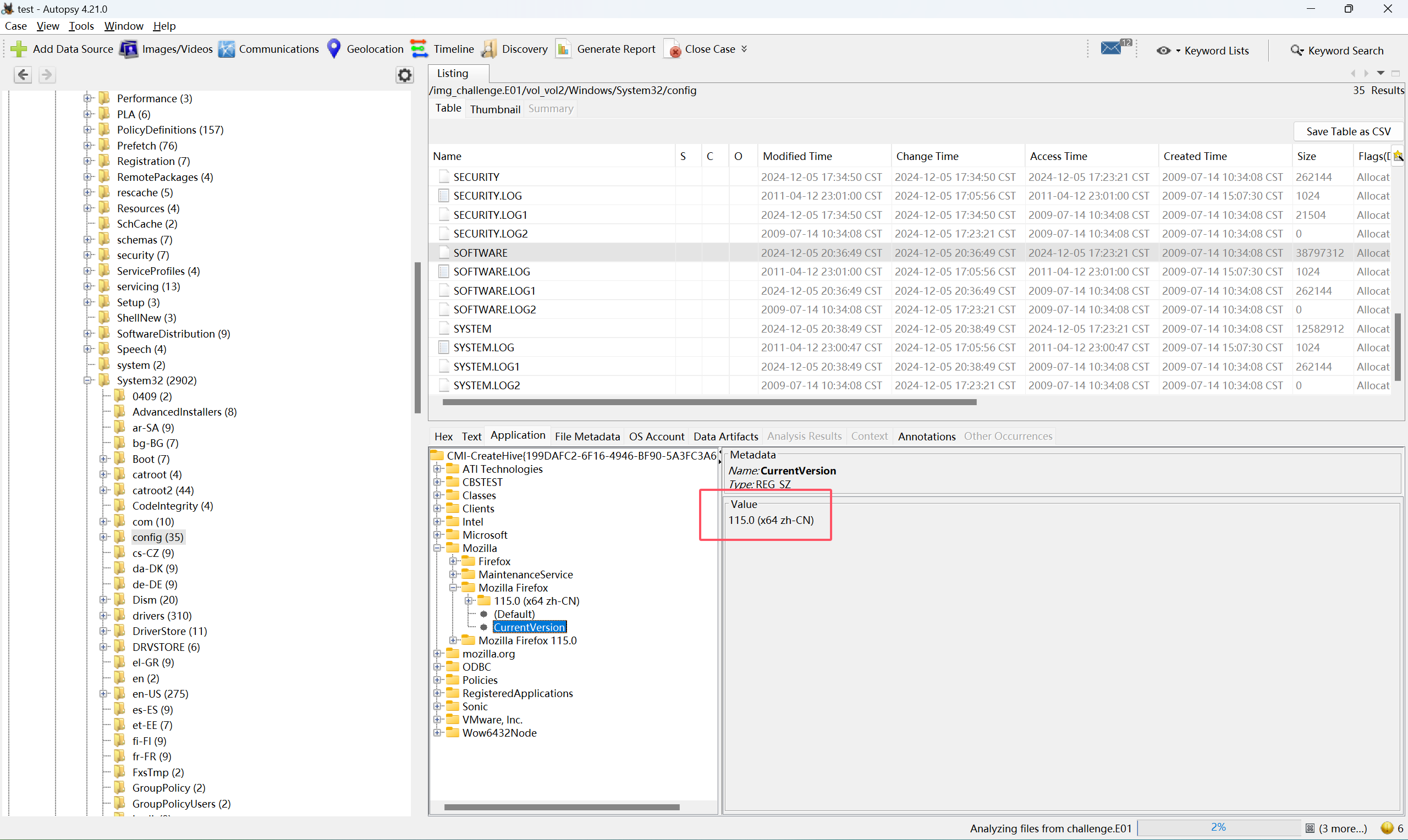
综上,压缩包的密码就是D0g3xGC_Windows_7_Ultimate_115.0,解压后可以得到下面这段密文
|
|
赛后知道了这是vbe格式加密后的密文,直接使用以.vbe格式保存,再用在线网站解密即可
打开解密完成的vbs文件即可得到flag2
|
|
然后回到Autopsy中继续看,可以找到一个加密的Original.zip
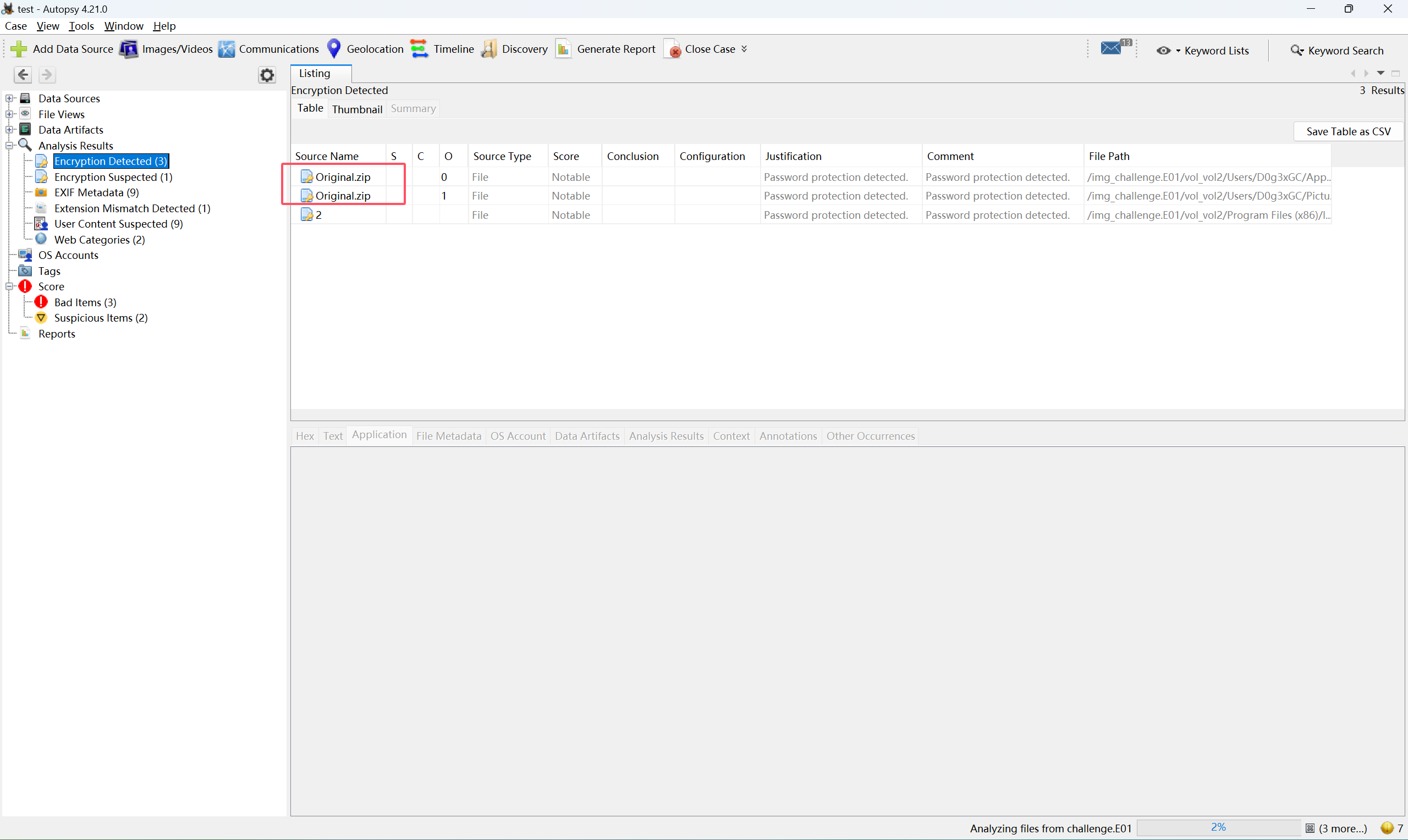
压缩包的路径为C:/Users/D0g3xGC/Pictures/Original.zip
并且发现同一路径下还有一个CatWatermark_666.png的可疑图片
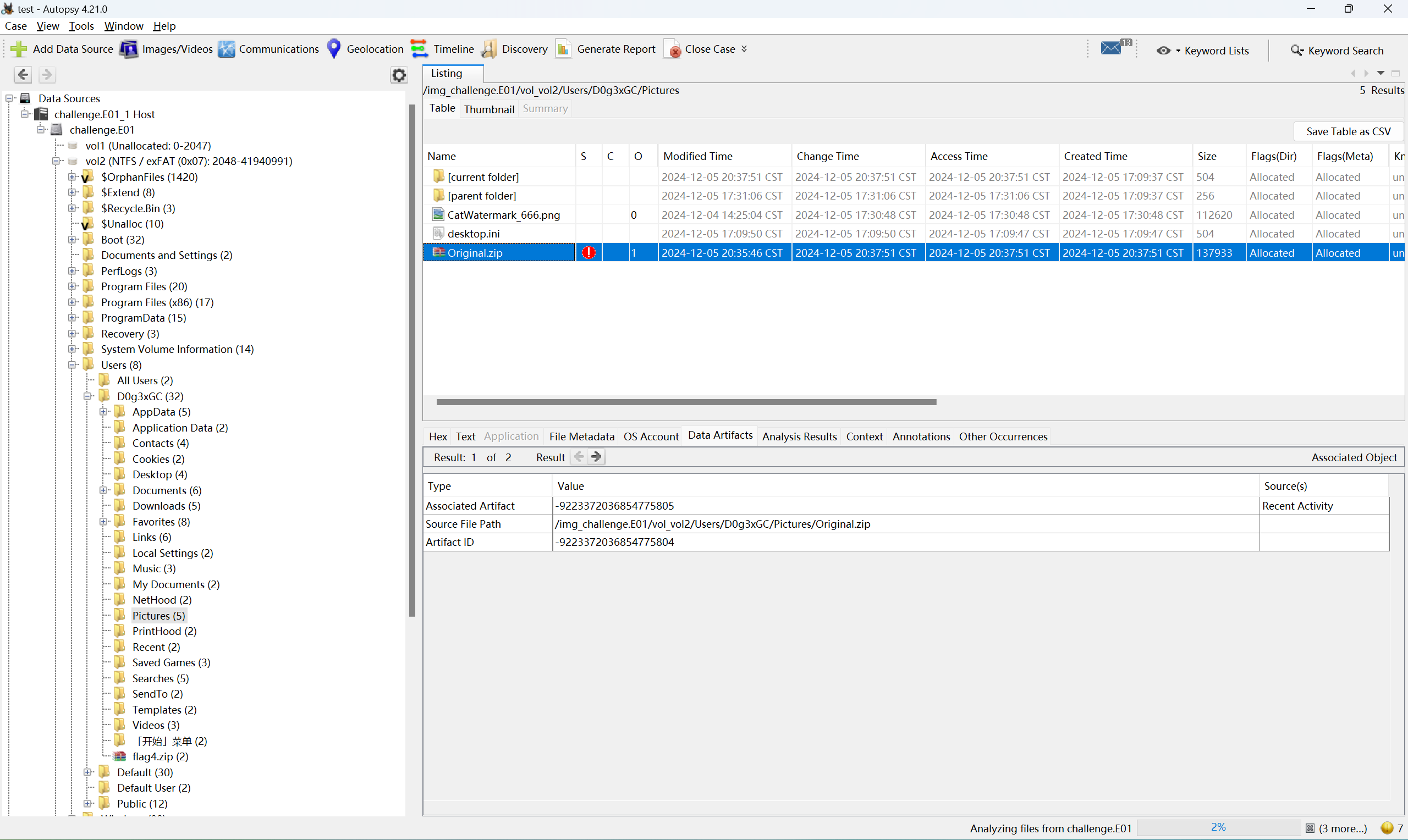
尝试把两个文件都提取出来,压缩包发现是一个加密的,注释中有关于密码的提示
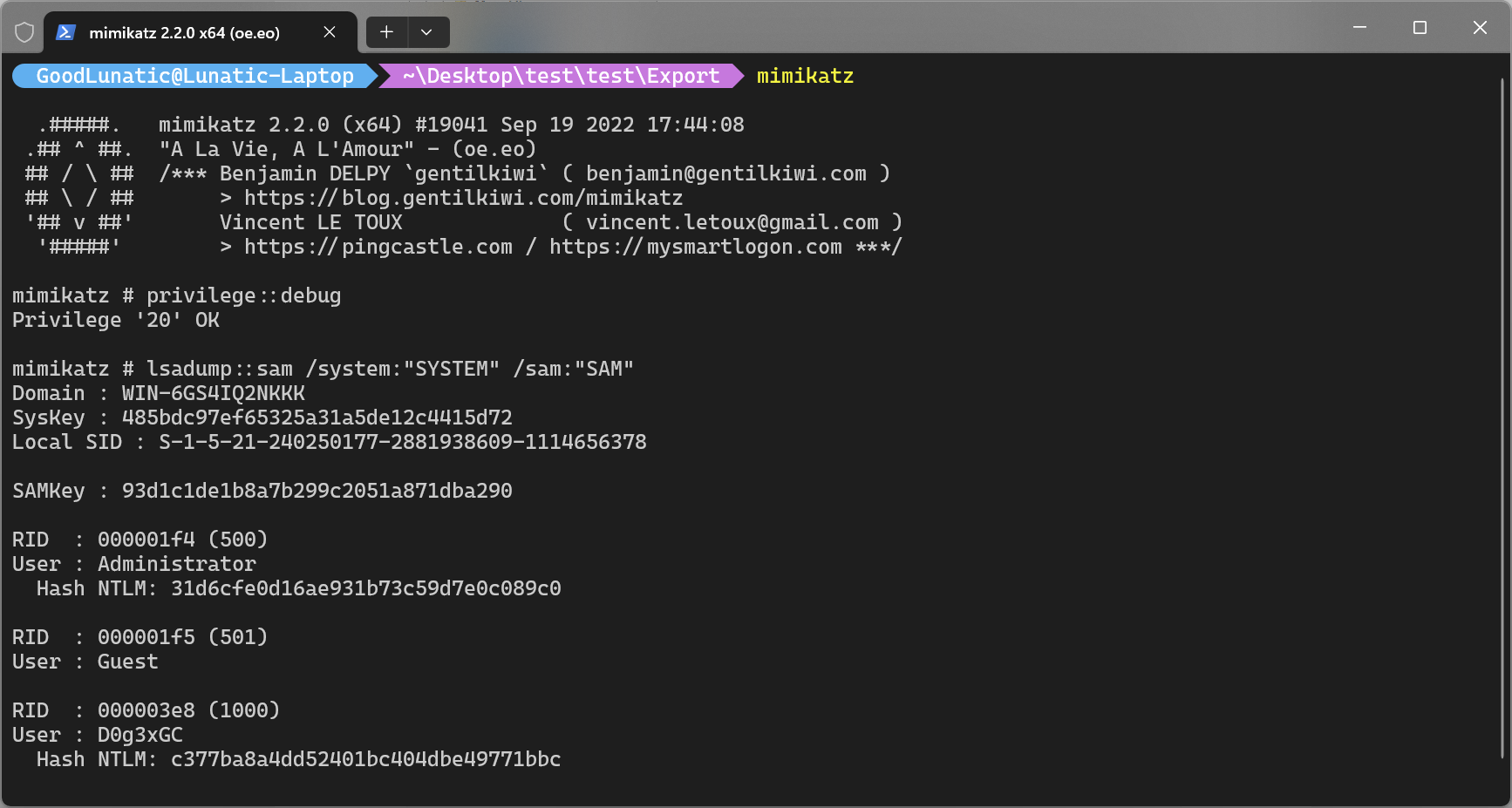
对于用户的登录密码,我们可以导出C:\Windows\System32\config目录下的SYSTEM和SAM两个文件
然后用mimikatz抓取hash,可以得到用户D0g3xGC用户的NTLM哈希为c377ba8a4dd52401bc404dbe49771bbc
拿到NTLM哈希后可以选择使用Hashcat爆破或者直接使用在线网站查询
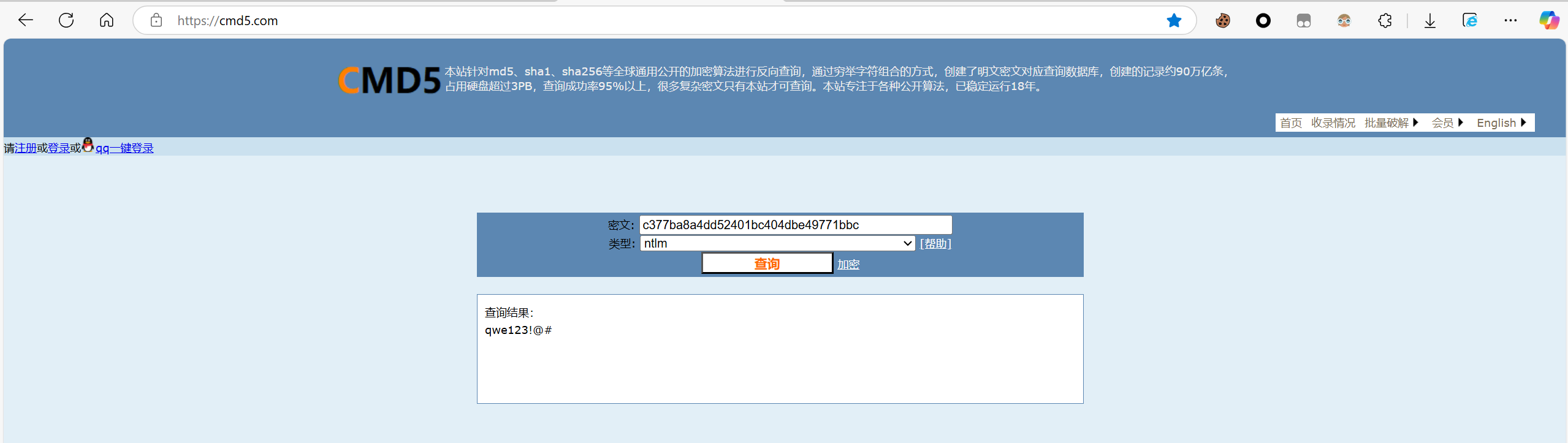
CMD5上可以直接查找密码为:qwe123!@#
然后我们需要获取用户登录otterctf网站的密码,结合之前发现这个系统中存在firefox,因此大概就是火狐浏览器登录凭证取证了
火狐的登录凭证可以参考这个开源项目进行破解,运行脚本后即可得到密码:Y0u_f1Nd^_^m3_233
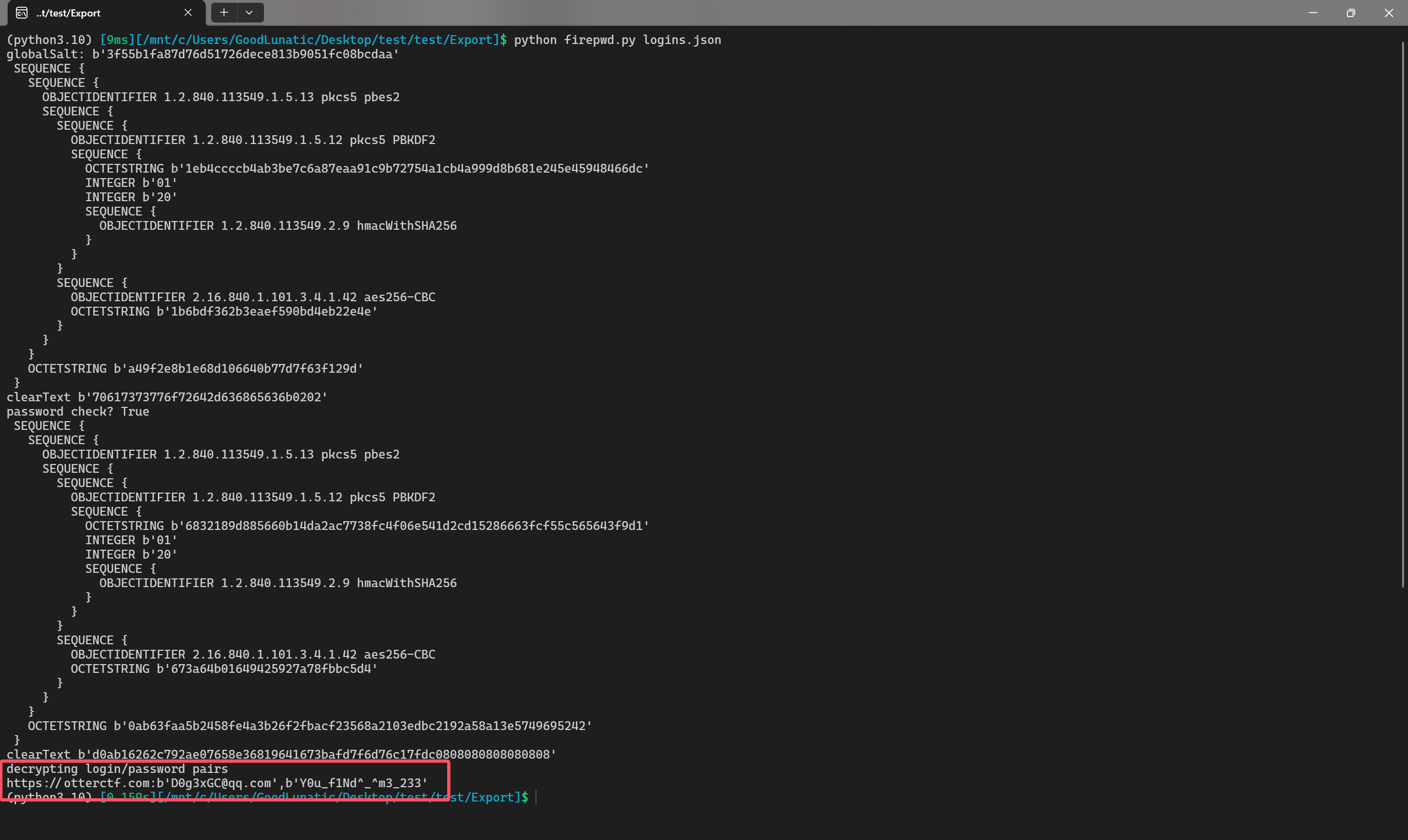
因此最后的解压密码为qwe123!@#_Y0u_f1Nd^_^m3_233,解压压缩包后得到一张Original.png
结合之前的提示CatWatermark_666.png,可以使用CatWatermark这个开源项目进行解密
参考项目中的Usage,发现解密需要提供arnold_dx arnold_dy arnold_rd这三个参数,结合图片名称,猜测三个参数应该就是6 6 6
|
|
所以直接把项目下载到本地然后Decode即可得到flag3:F1N4L_s3CR3t_0F_Th15_
|
|
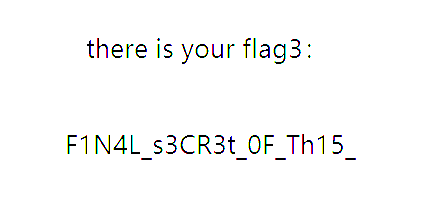
综上,结合上述四段flag,本题完整的flag为:D0g3xGC{Y0u_h4V3_f0und_7H3_F1N4L_s3CR3t_0F_Th15F0R3N51c5_Ch4Ll3N93}
一些个人的碎碎念:
感觉这题取证确实出的挺好的,可以看出来出题人花了挺多心思,结合了挺多知识点
感觉可以作为一道考察取证基础的典型例题了
题目名称 eZ_Steg0
解压题目附件,可以得到以下几个文件,其中key.zip是加密的,猜测密码藏在图片中
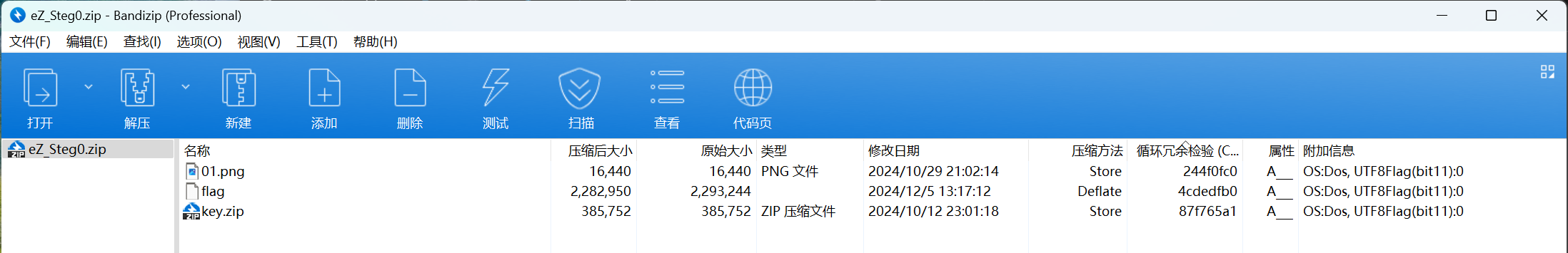
打开01.png,发现都是二值化的图像

写一个脚本提取一下里面的数据,发现是PNG图片的十六进制数据
|
|
运行以上脚本可以得到下图,因此压缩吧密码就是:!!SUp3RP422W0RD^/??.&&
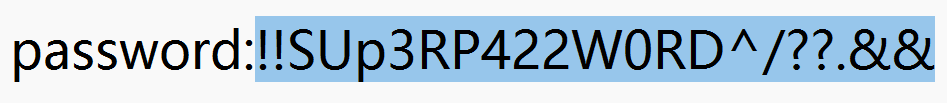
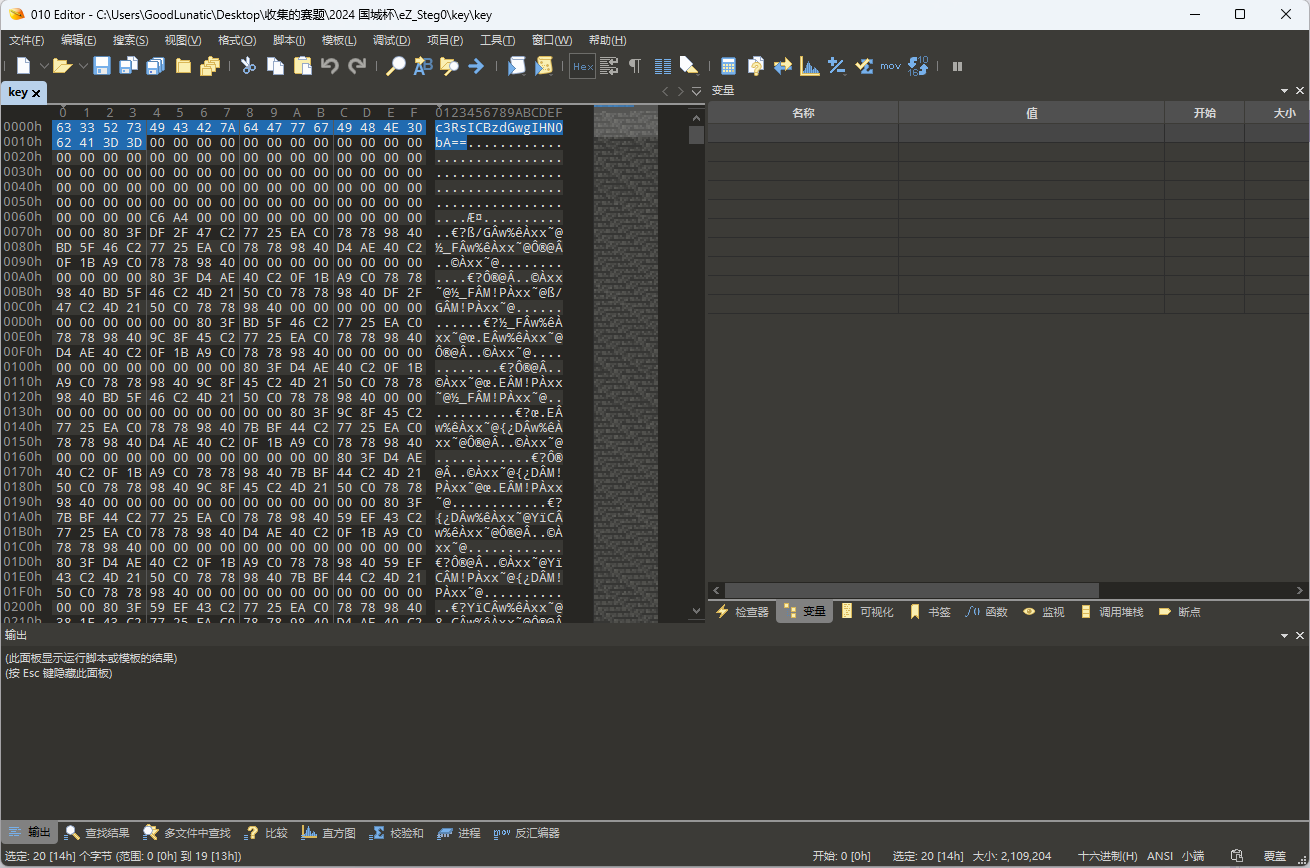
使用得到的密码解压压缩包,可以得到一个未知类型的key文件
010打开发现前面有一段base64编码
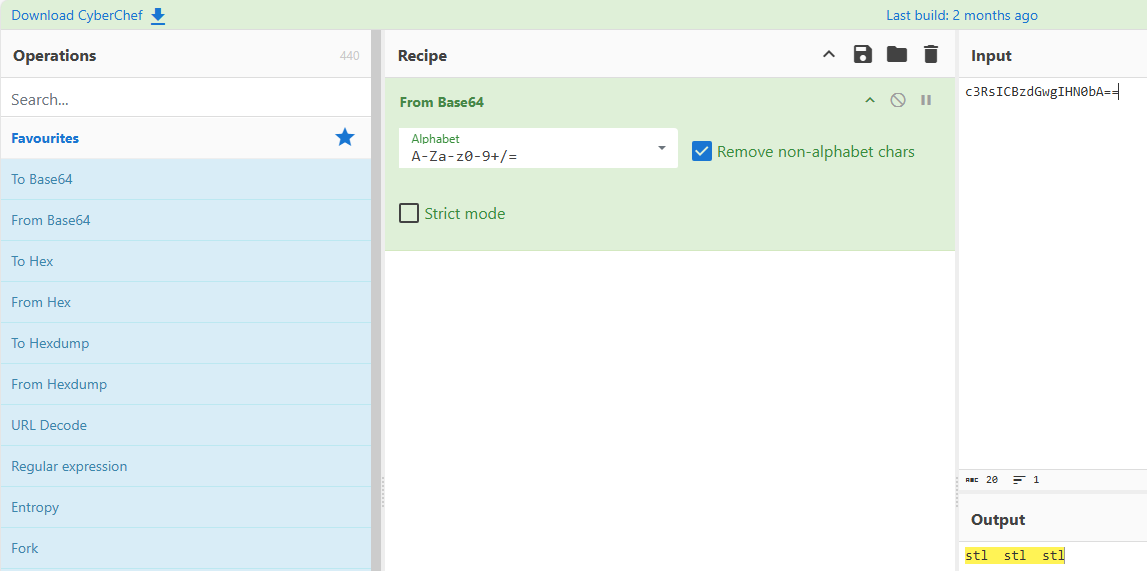
CyberChef解码一下可以得到提示:stl stl stl
上网搜索一下stl文件,发现是一种三位图形文件格式
可以直接用这个在线网站打开
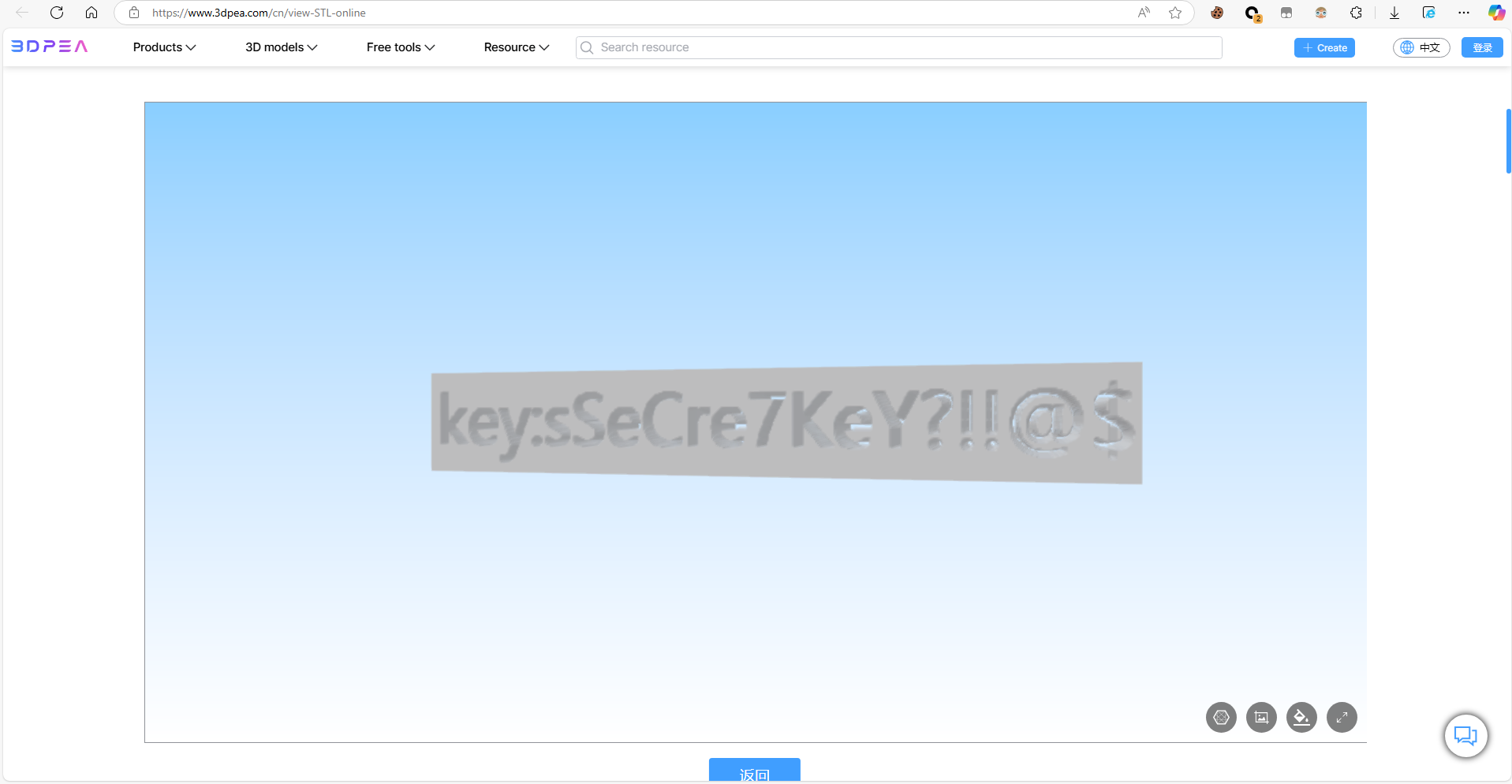
得到一个密钥:sSeCre7keY?!!@$,用这个密钥去异或一下flag文件,可以得到一个wav
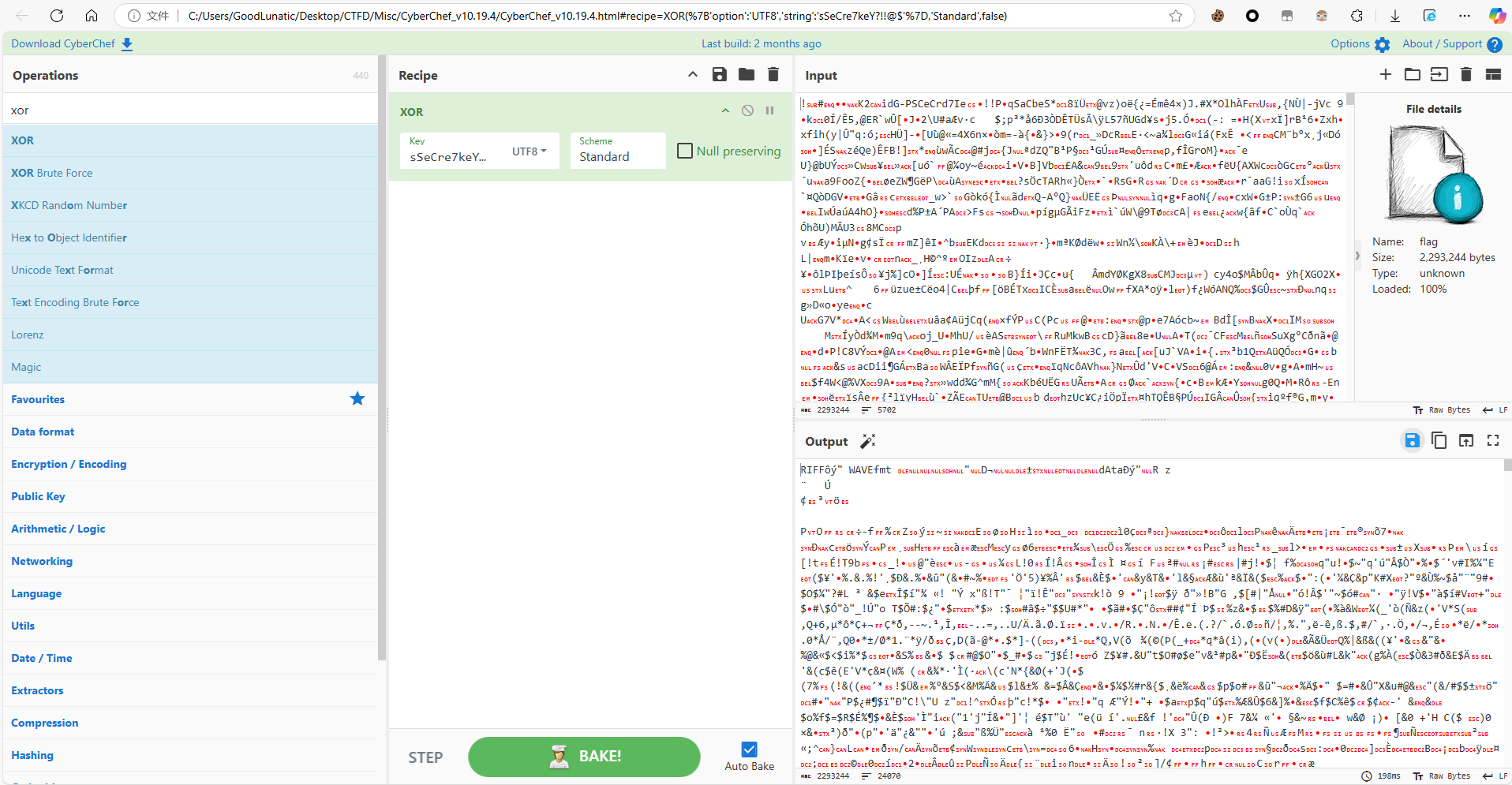
用010打开得到的wav文件,提示dAta有问题
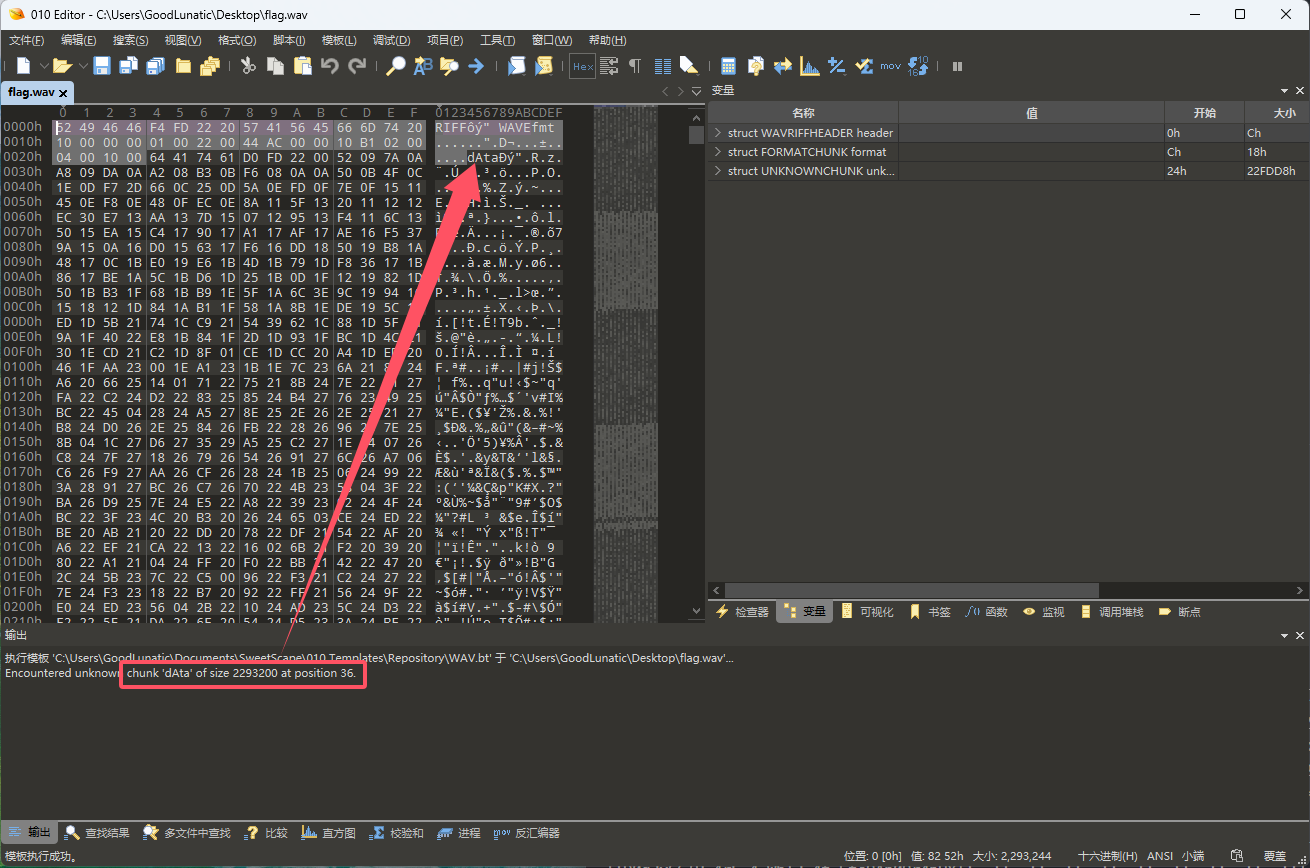
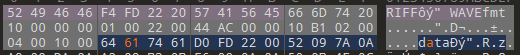
找一个正常的wav,发现把dAta改成data就正常了
然后根据题面的提示,猜测是wav文件的LSB隐写
编写以下脚本提取隐写的内容即可得到flag:D0g3xGC{U_4rE_4_WhI2_4t_Ste9An09r4pHY}
|
|
题目名称 保险柜的秘密(固件逆向)
附件给了一个demo1.hex和一个tips.txt,其中tips内容如下
- 这是一个提取自普通功耗的,使用Cortex-M3内核的72Mhz,48引脚,64kb闪存的保险柜芯片
- 摩斯密码常常用.和-来表示,且每一位中间都会被空格隔开
从tips中可以分析得到固件所用芯片为stm32f103c8t6
IDA32中打开反编译可以得到加密逻辑
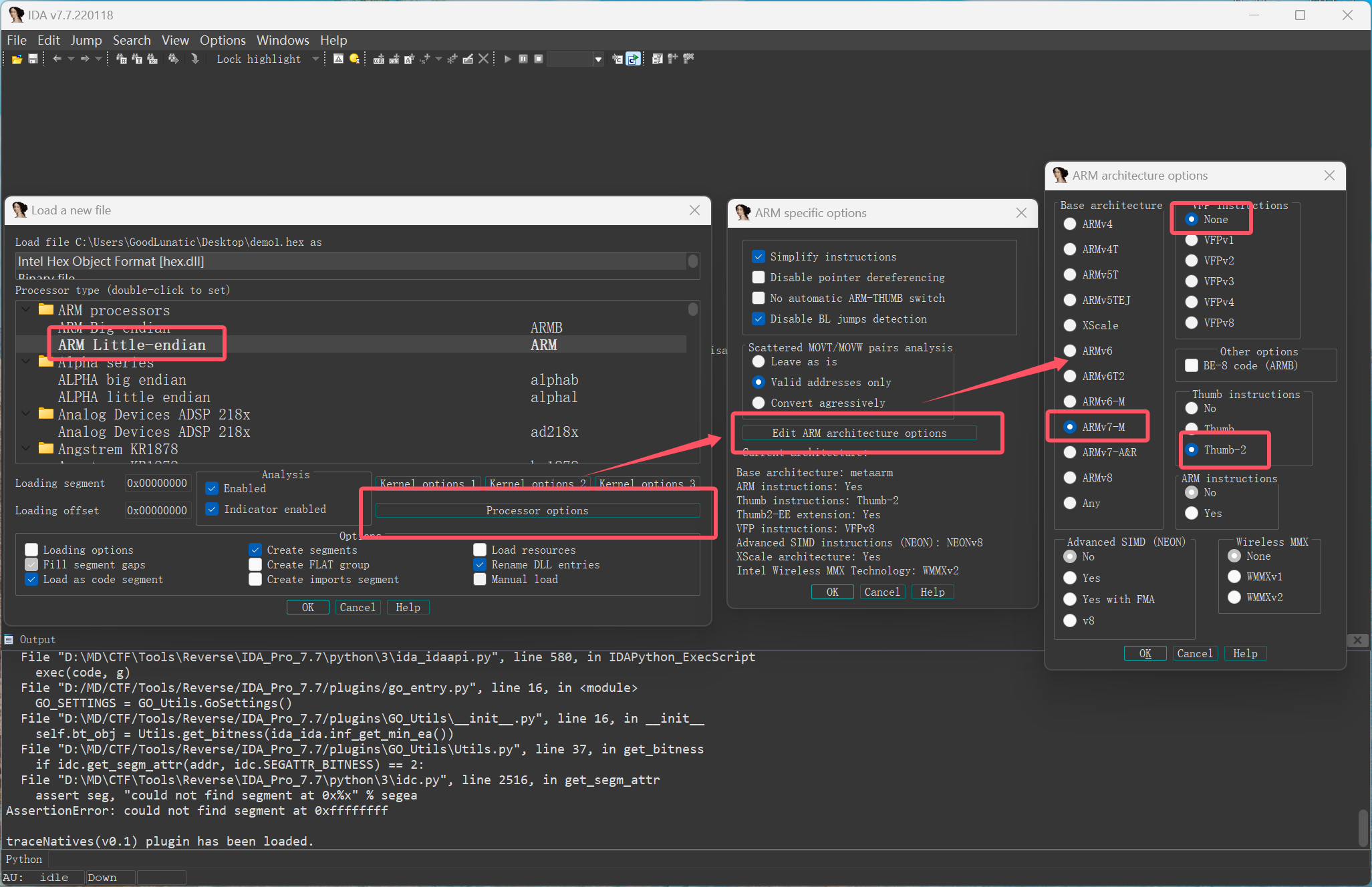
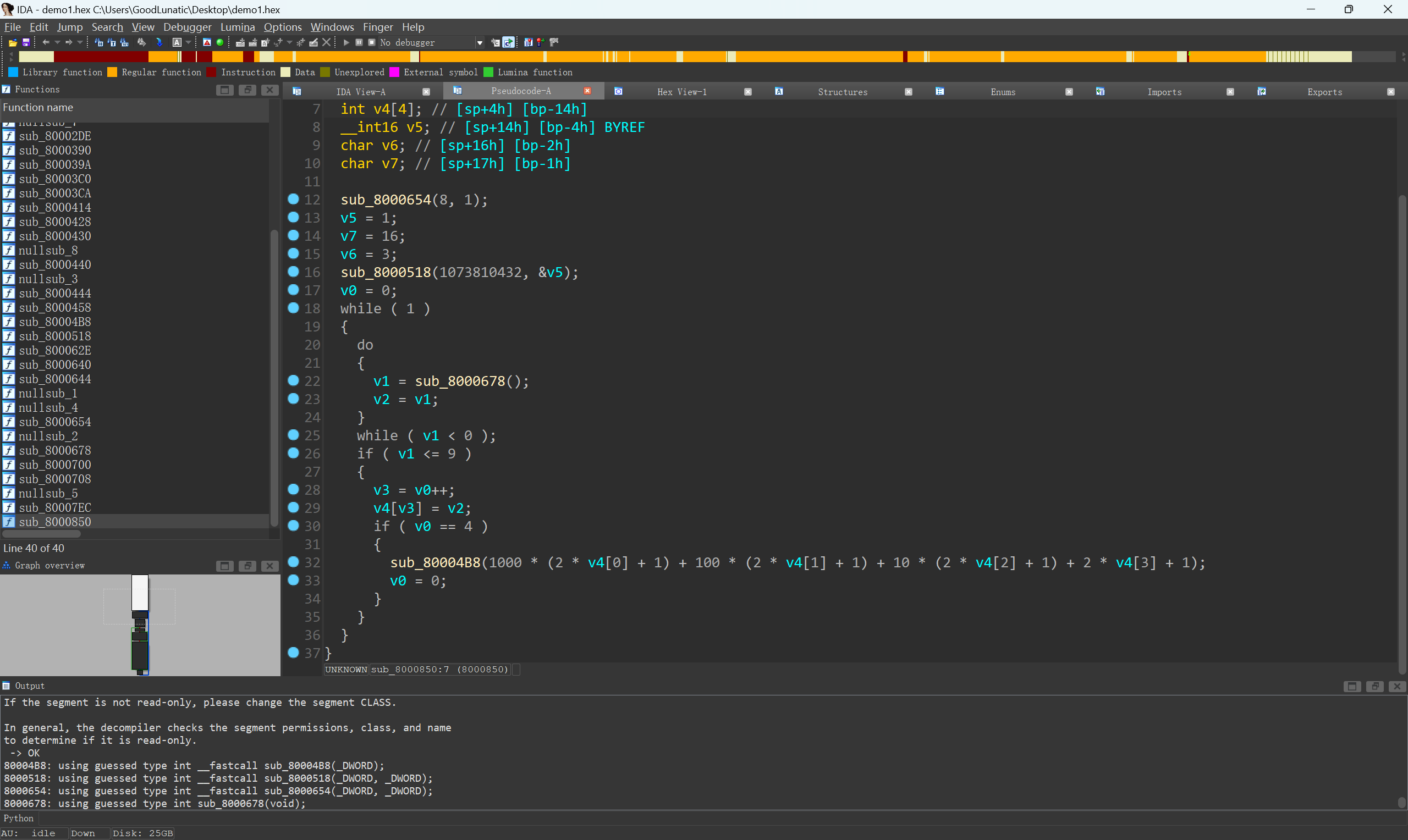
|
|
线下决赛
题目名称 d0_U_kn0w_J4v4
解压附件压缩包得到下图和一个加密的压缩包,猜测需要从图片中获得压缩包的解压密码

题目名称和图片的信息很明显的提示了我们是Java盲水印
因此我们直接用开源项目解密即可
https://github.com/ww23/BlindWatermark
|
|

得到压缩包的解压密码:A7f#9xQ!r3b$T
解压后得到一张名为reverse.png的二维码和一个flag.txt
我们给二维码反色然后扫码,用微信扫码甚至可以不用反色
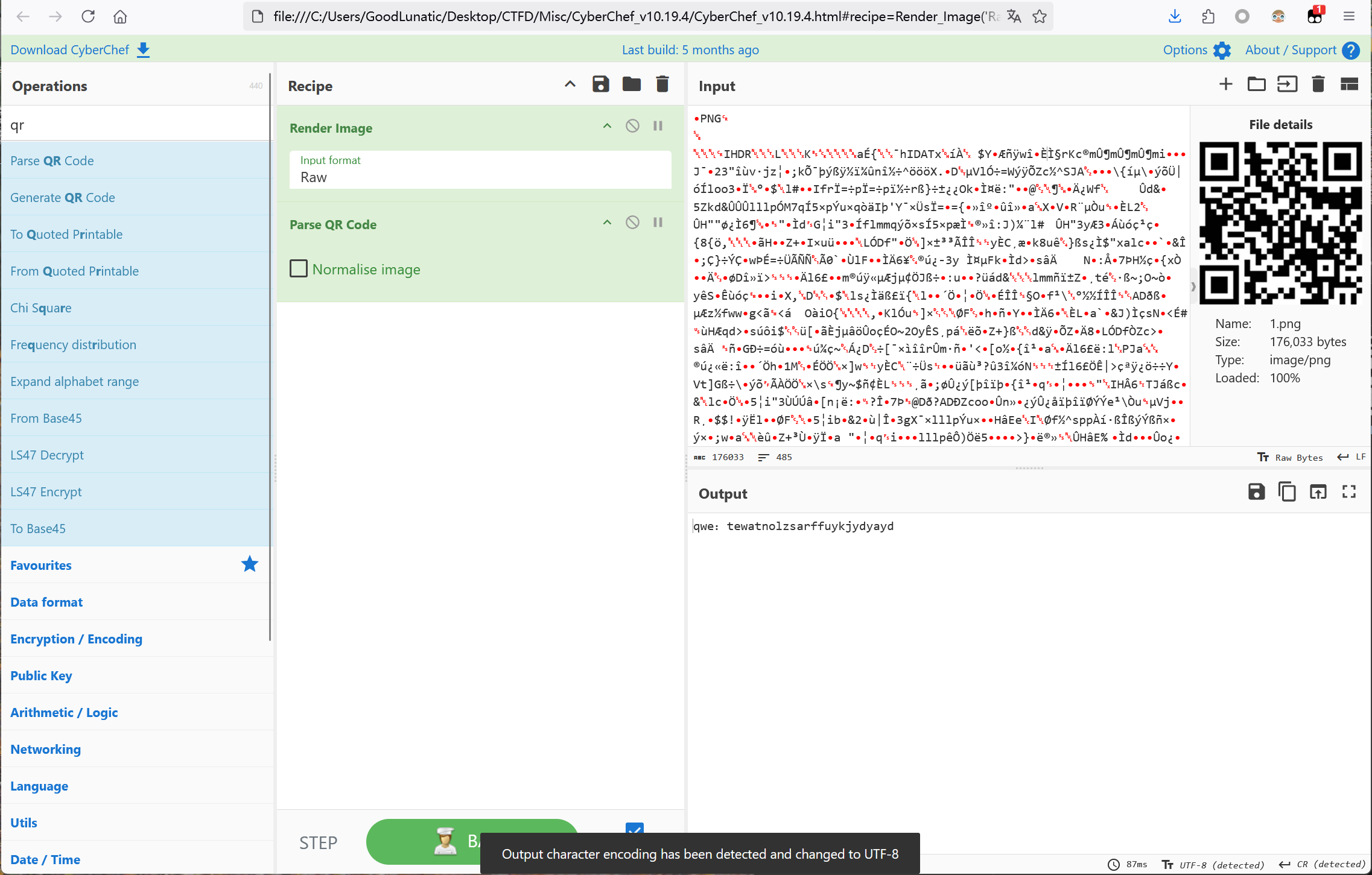
扫码得到:qwe:tewatnolzsarffuykjydyayd
然后在flag.txt中得到如下内容:
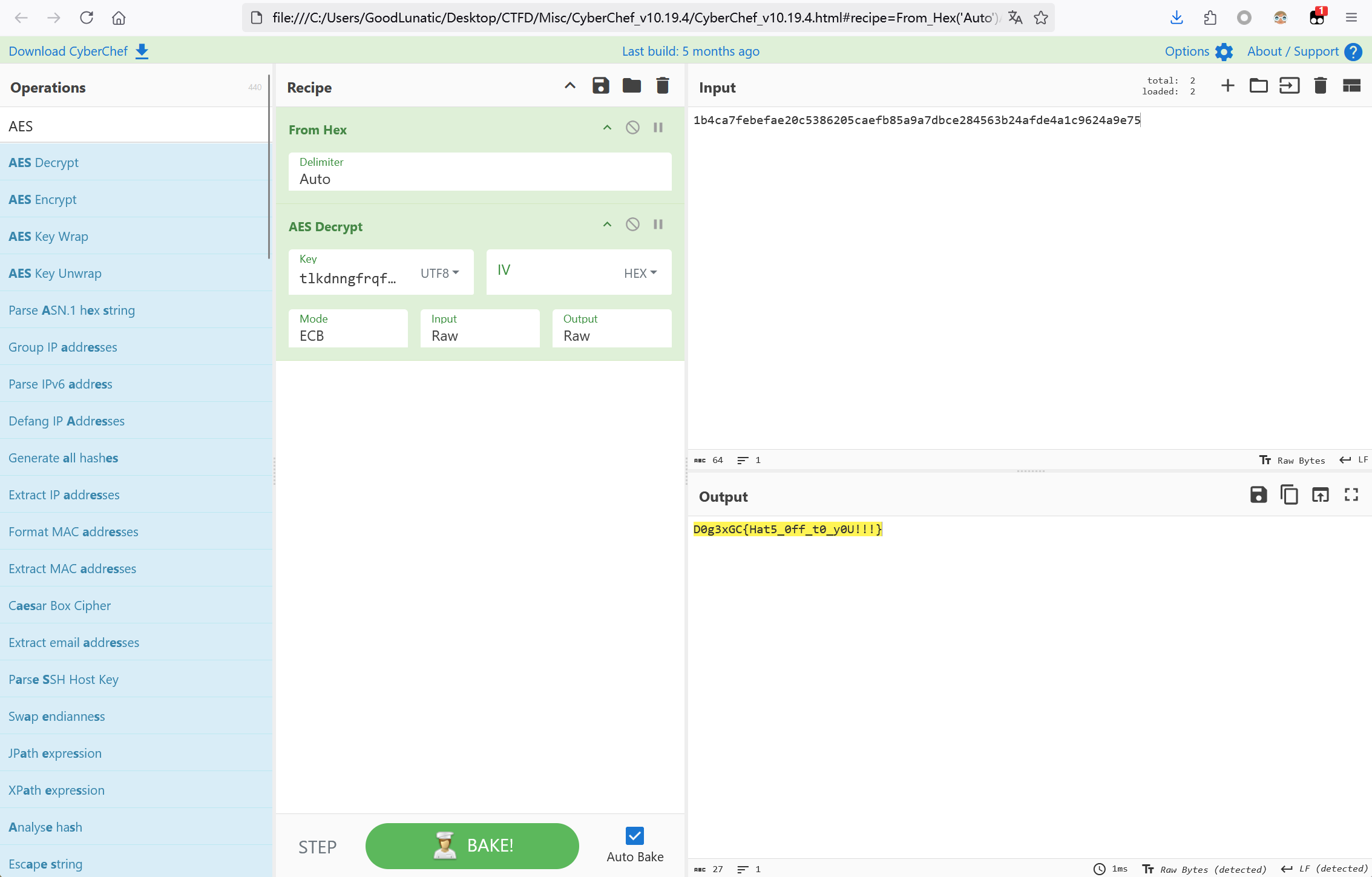
1b4ca7febefae20c5386205caefb85a9a7dbce284563b24afde4a1c9624a9e75
由qwe联想到键盘QWE密码,对照解密后得到:ecbkeyistlkdnngfrqfmfkfm

因此最后用得到的密钥解一个AES即可得到最后的flag:D0g3xGC{Hat5_0ff_t0_y0U!!!}
 Lunatic
Lunatic